What's new with Rumble 2.15? #
- Sync assets, software, and vulnerability data from Rapid7 InsightVM and Nexpose
- Quickly identify and report externally exposed assets and services
- Navigate your inventory faster with an updated Rumble Console
Gathering vulnerability data from Rapid7 #
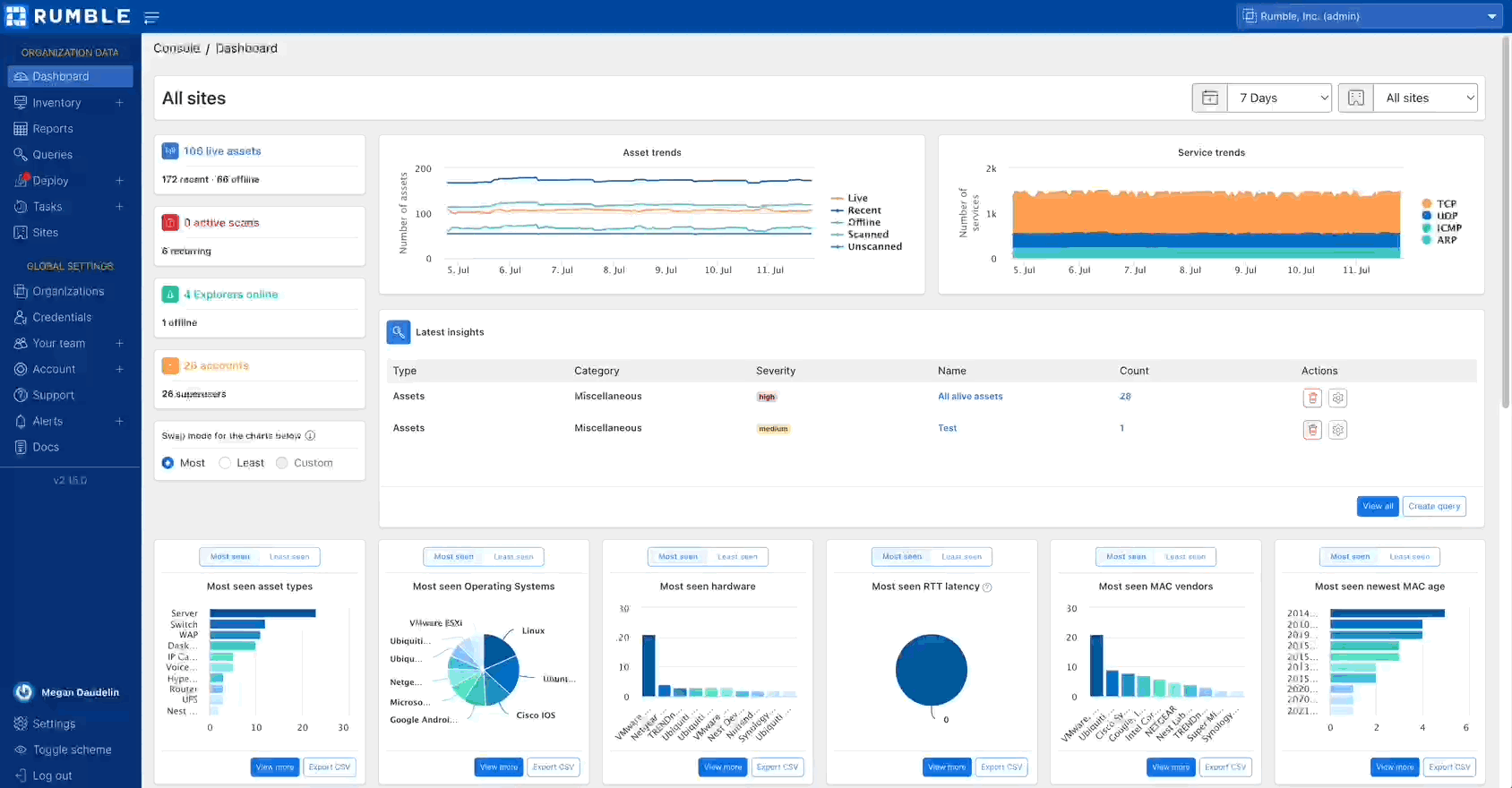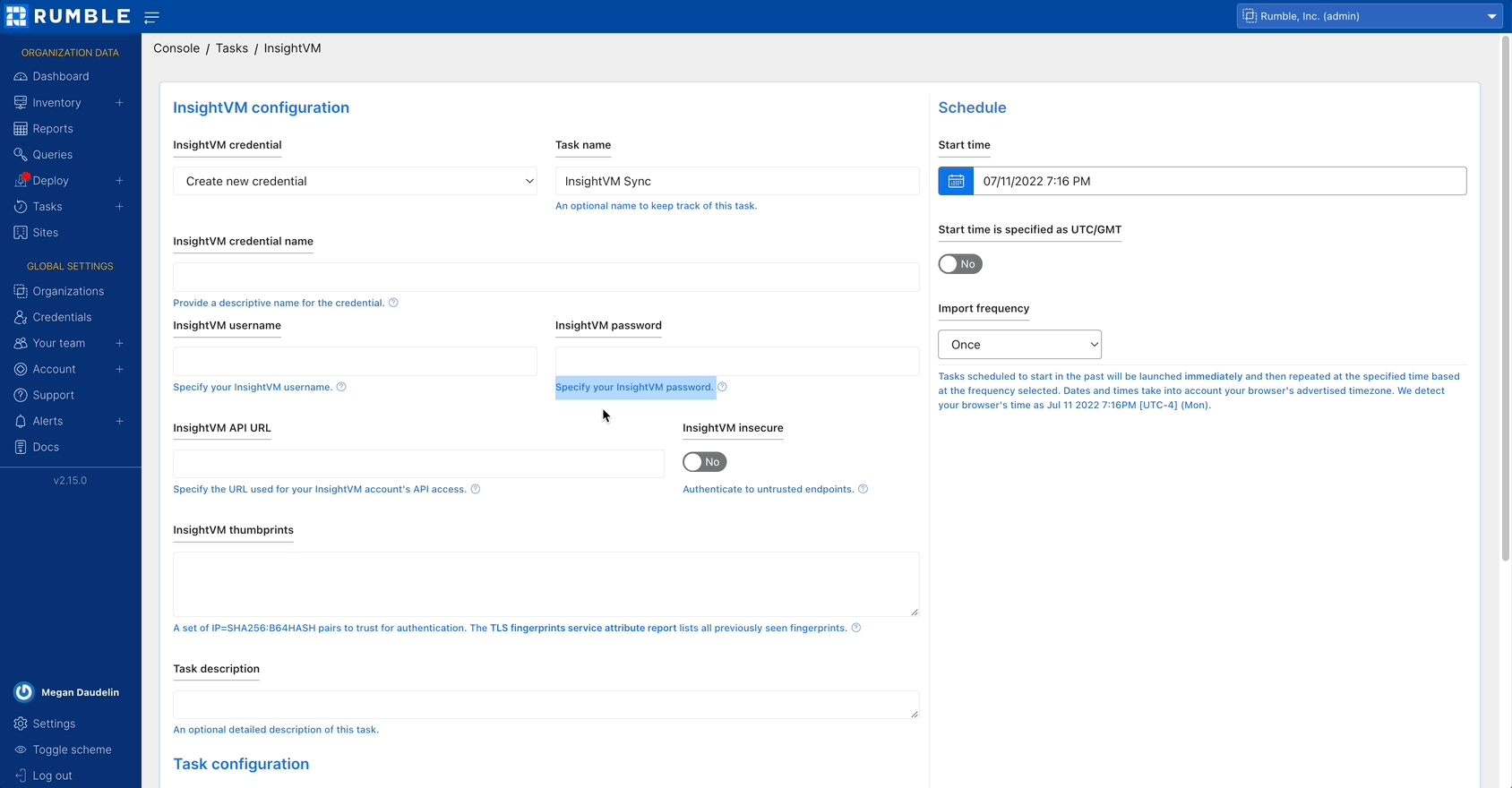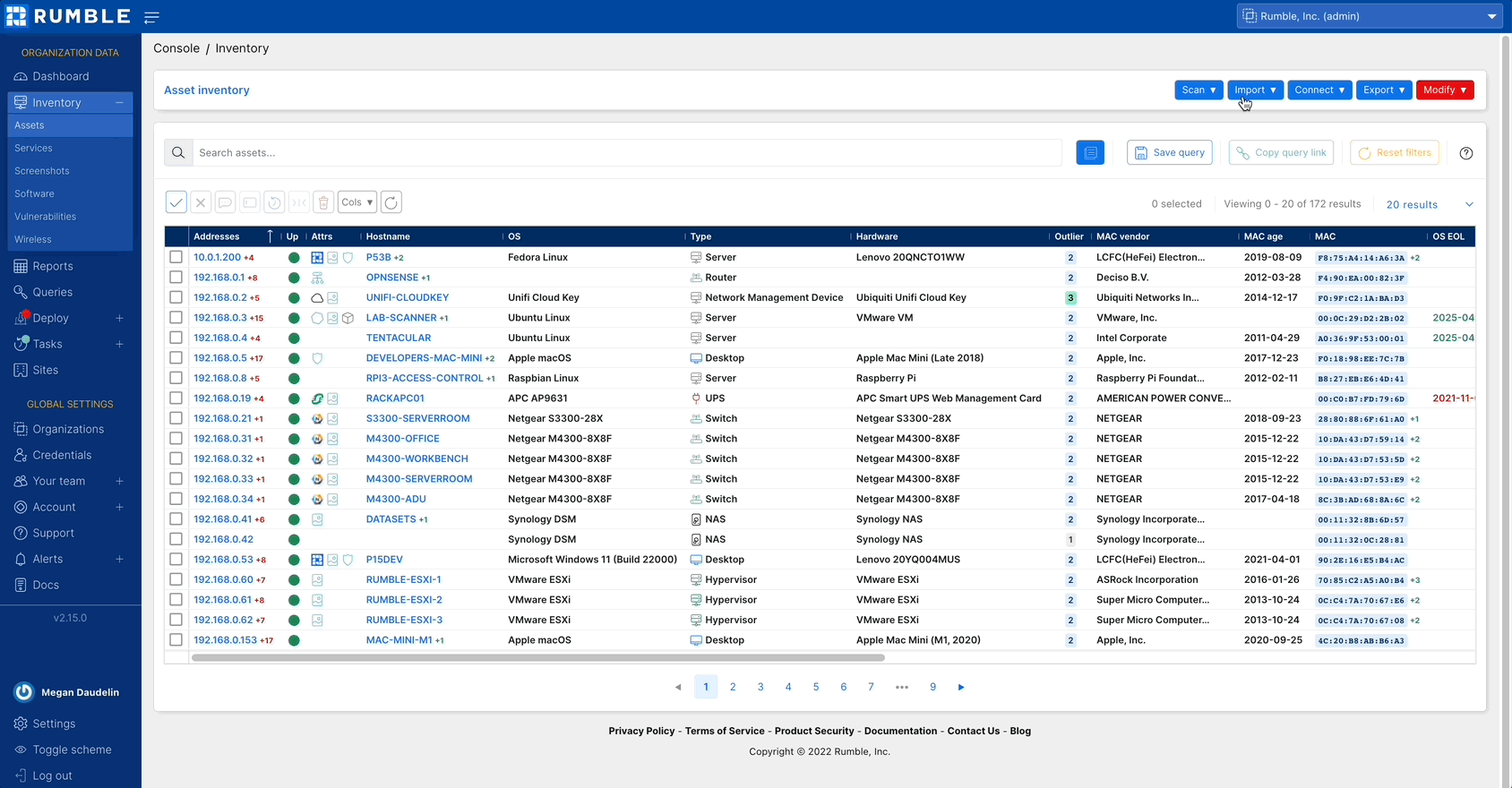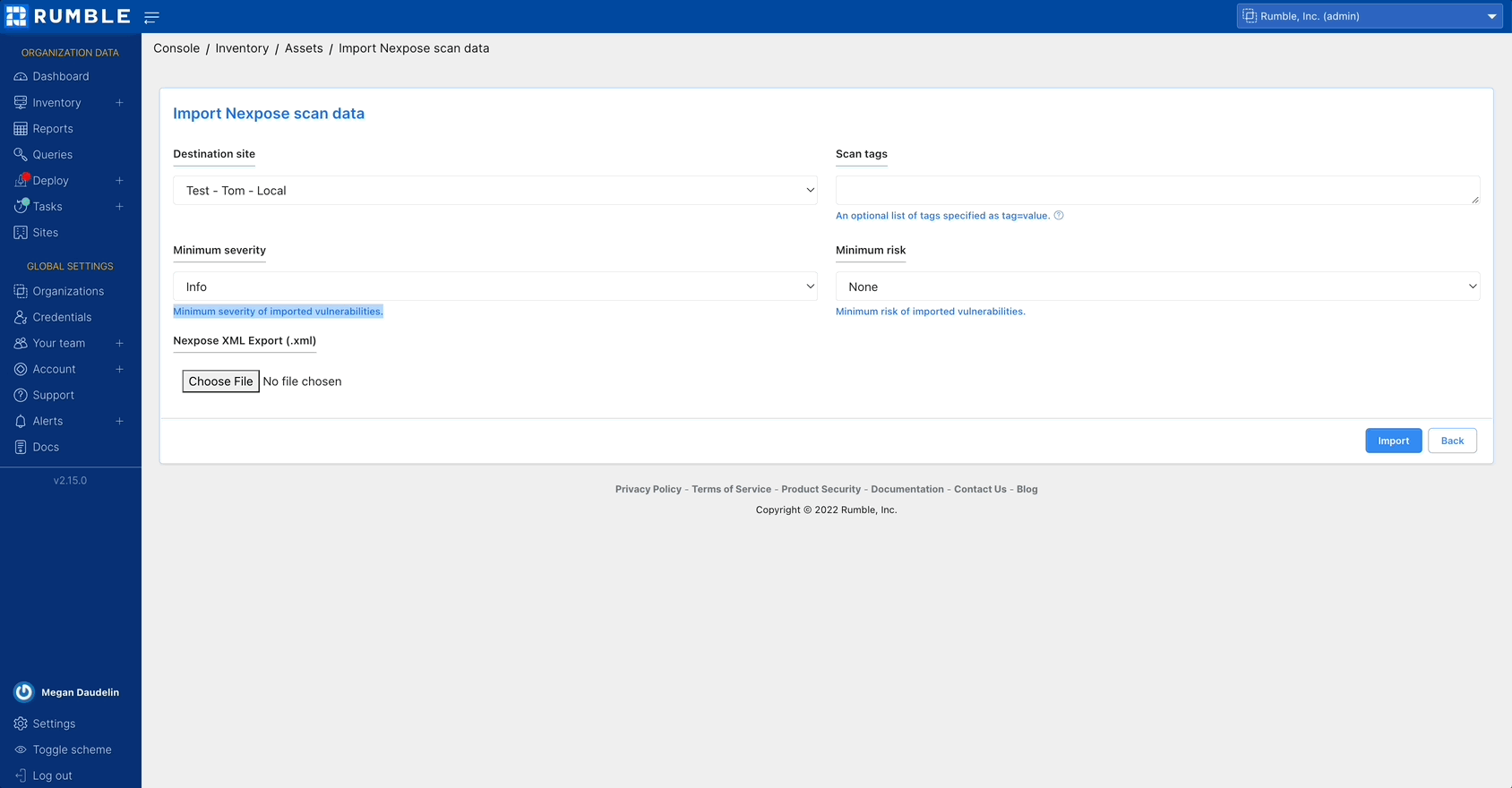
Rumble Enterprise users can now enrich their inventory with an authenticated API connection to InsightVM or a file import from Nexpose. This allows you to search for Rapid7 attributes, software entries, and vulnerabilities in Rumble, as well as find assets not scanned by InsightVM or Nexpose. Rumble automatically correlates Rapid7 assets to Rumble assets based on unique fields. Vulnerability data can be viewed in the asset detail view as well as the vulnerability inventory tab. Vulnerability attributes include CVSS score, relevant CVEs, vulnerability description, and any recommended remediations.
To get started, set up an API connection to InsightVM or import an XML report file from Nexpose.
Connecting to Nessus Professional #
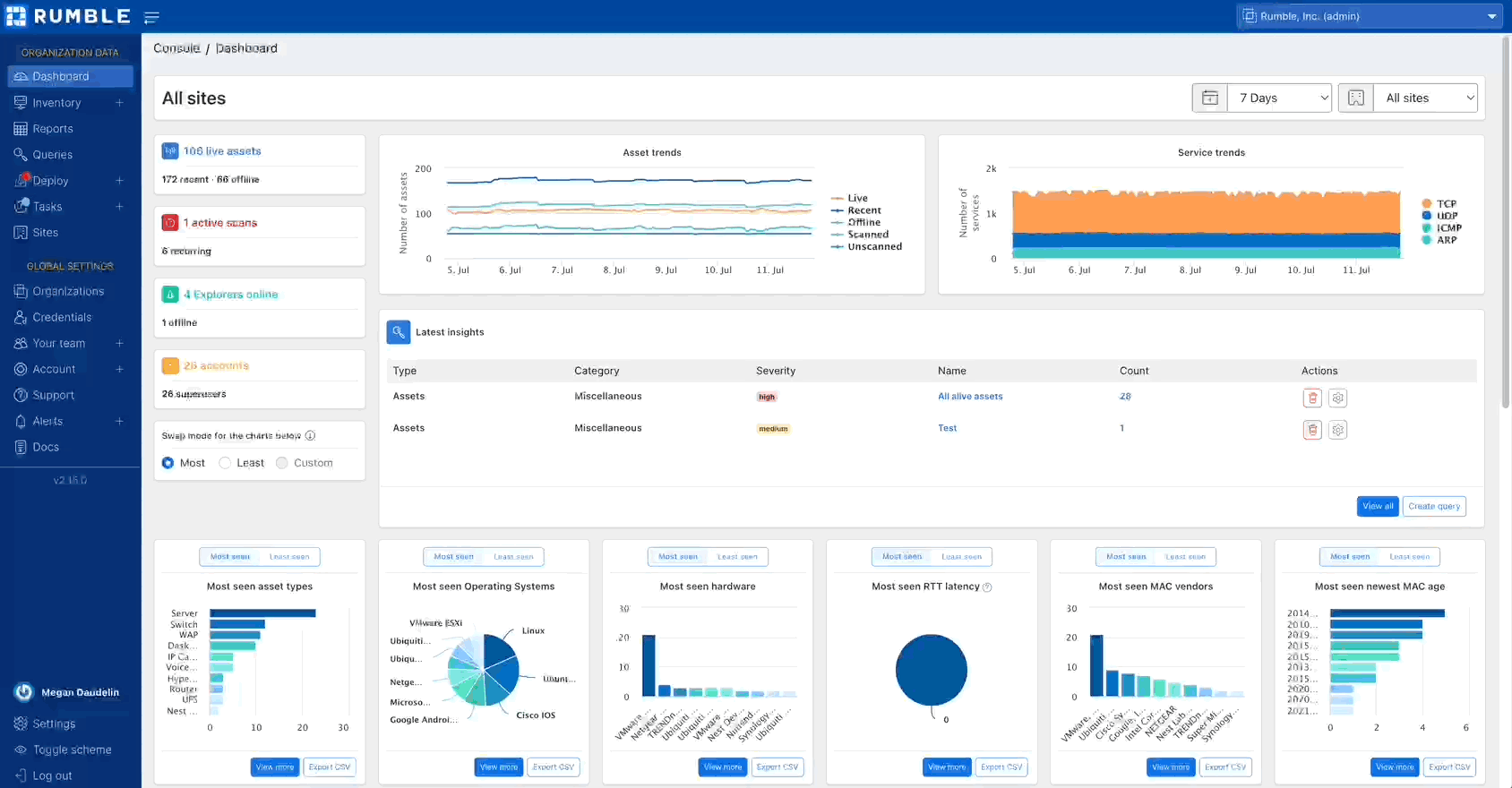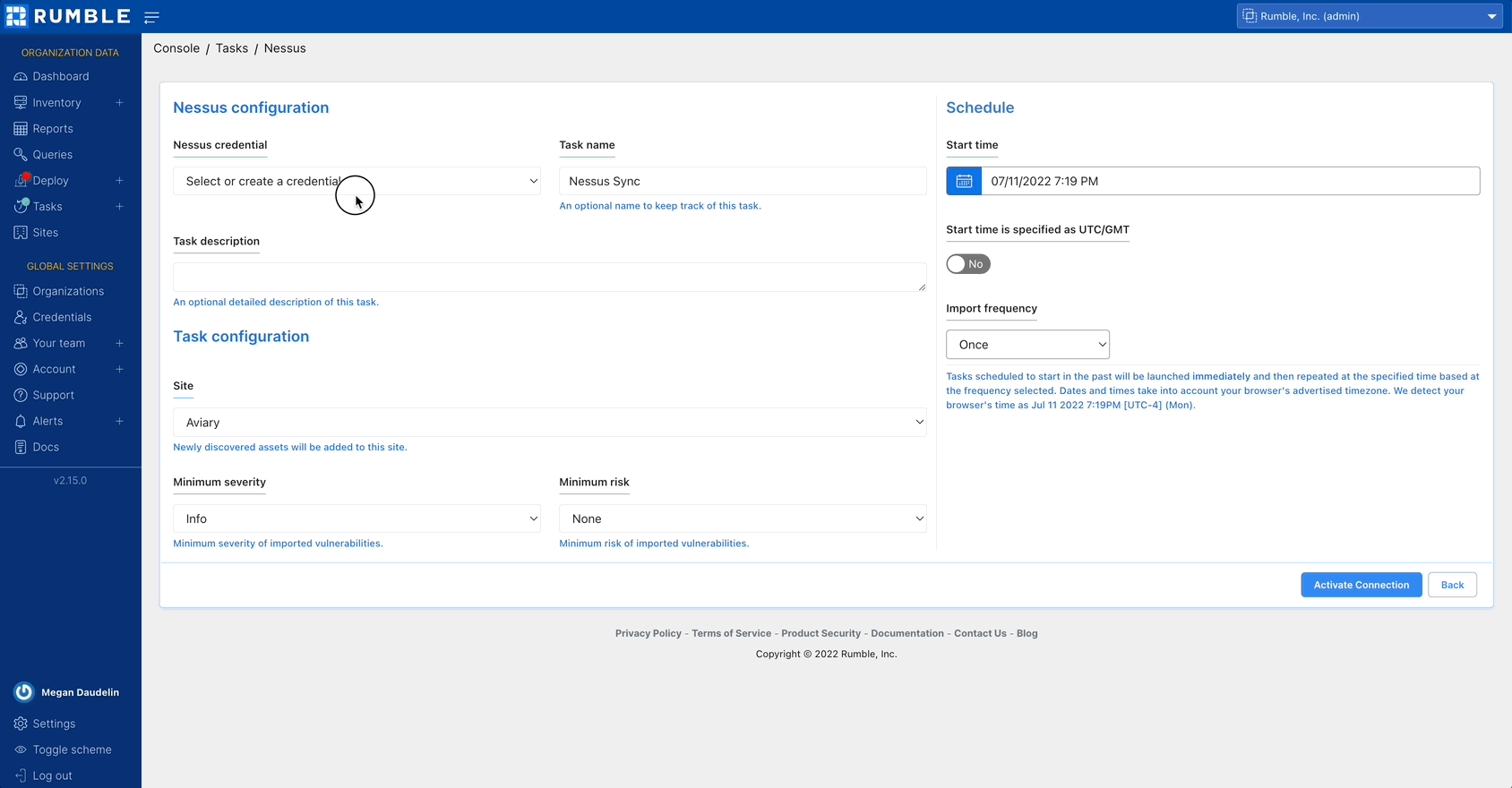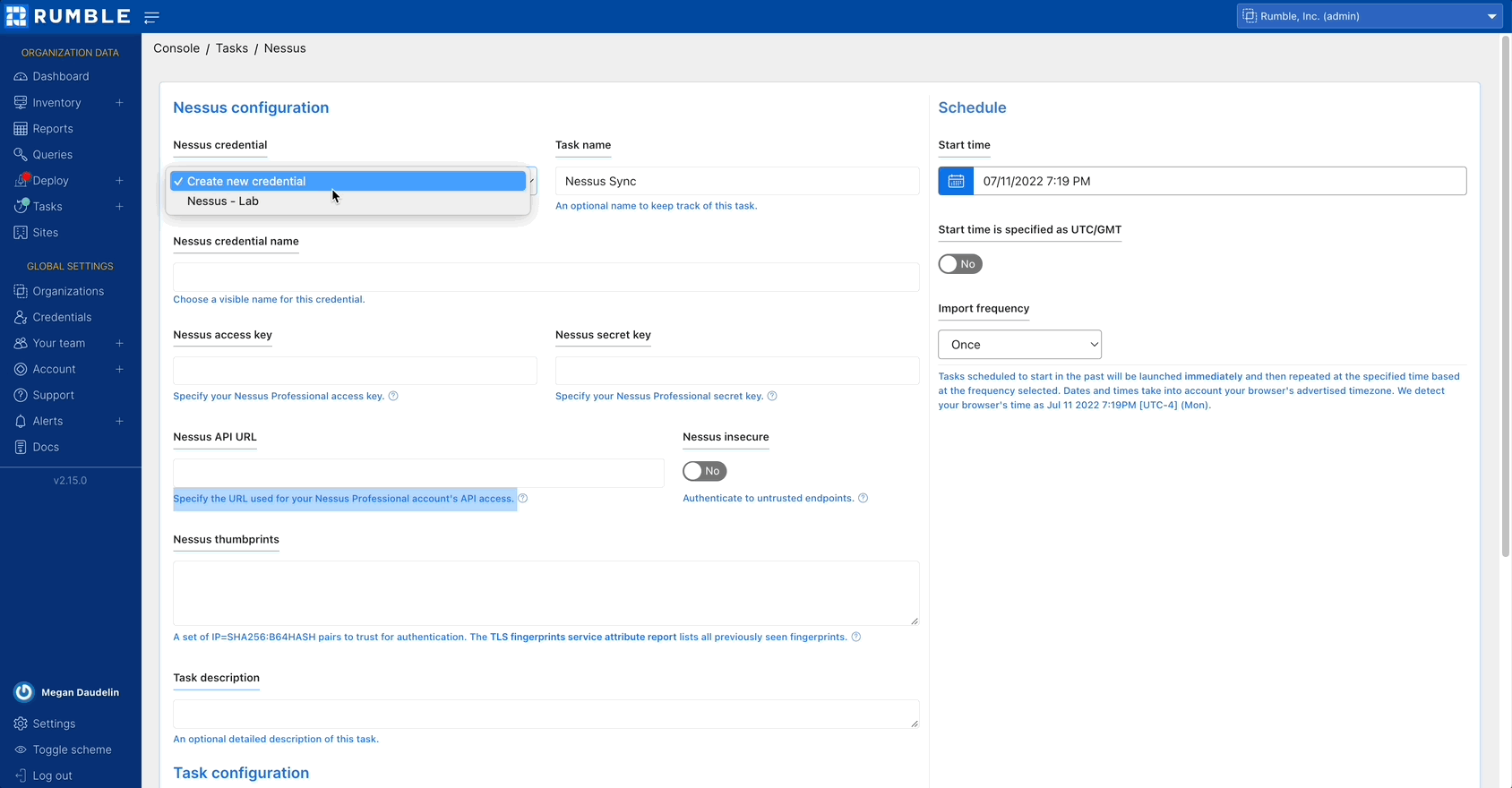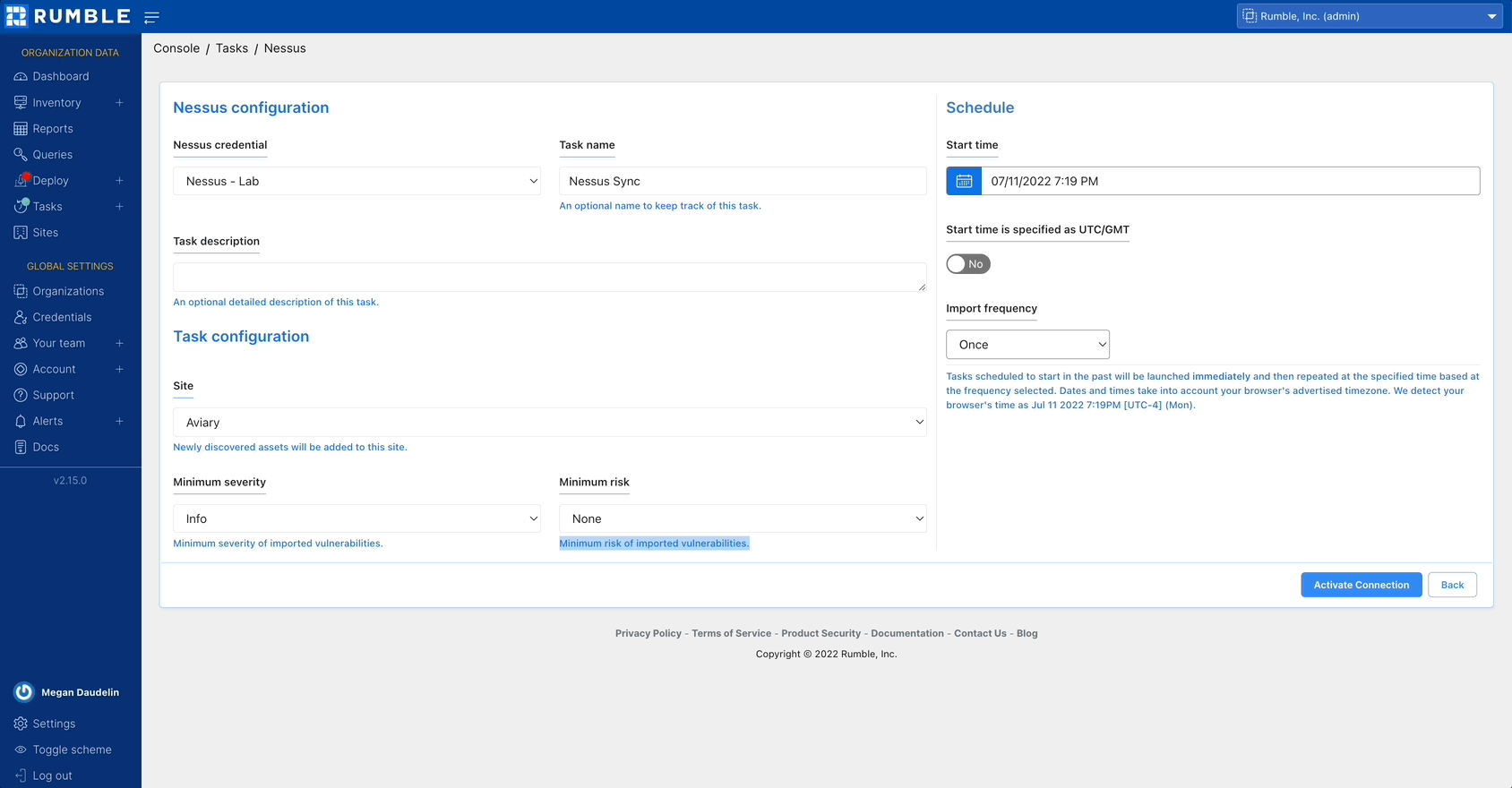
The Tenable integration now supports connecting to the Nessus Professional API. The integration can be run as a scan probe to gather vulnerability data from your onsite Nessus Professional instances.
Set up the Nessus Professional integration by creating a credential and running a scan.
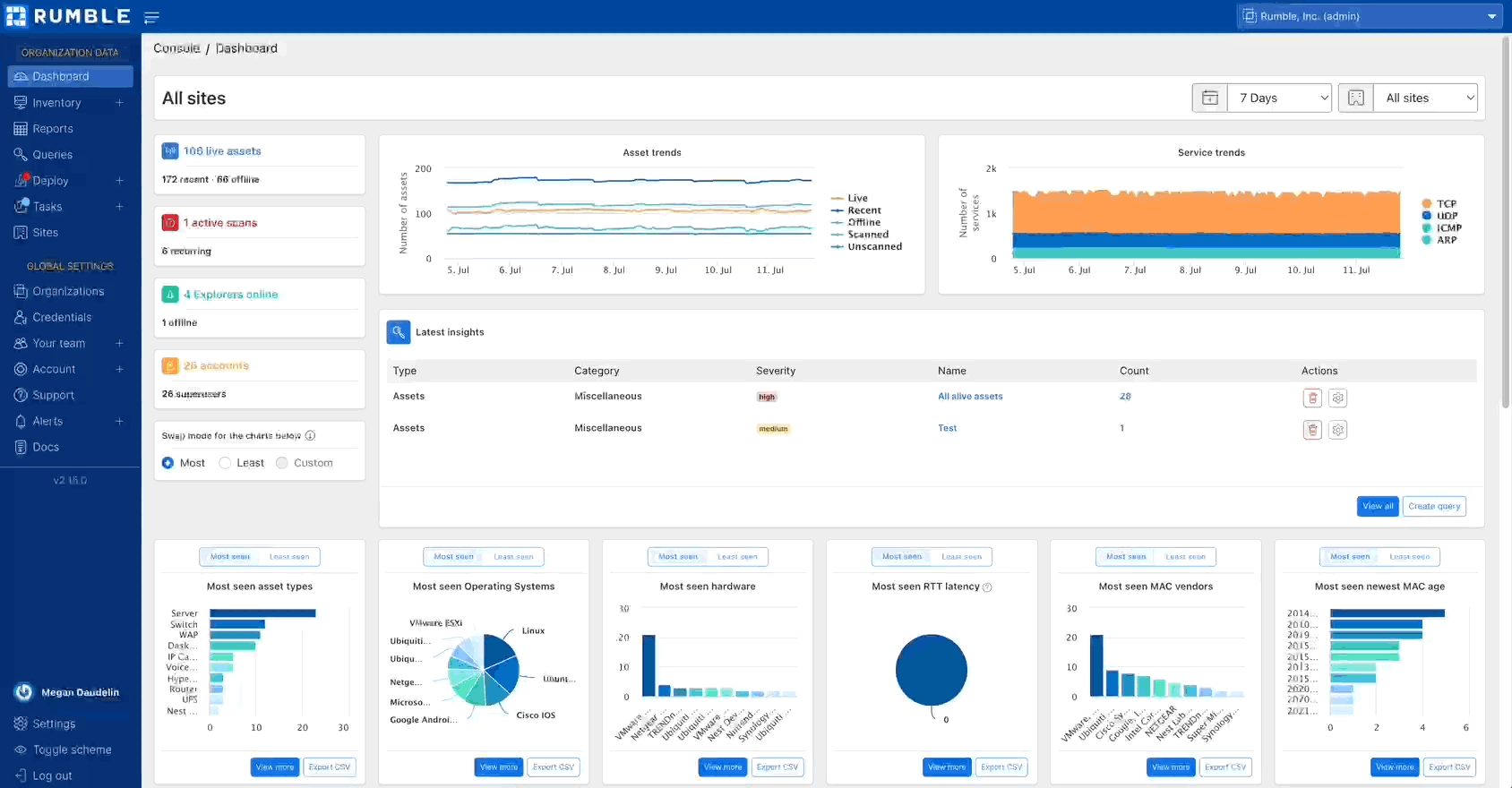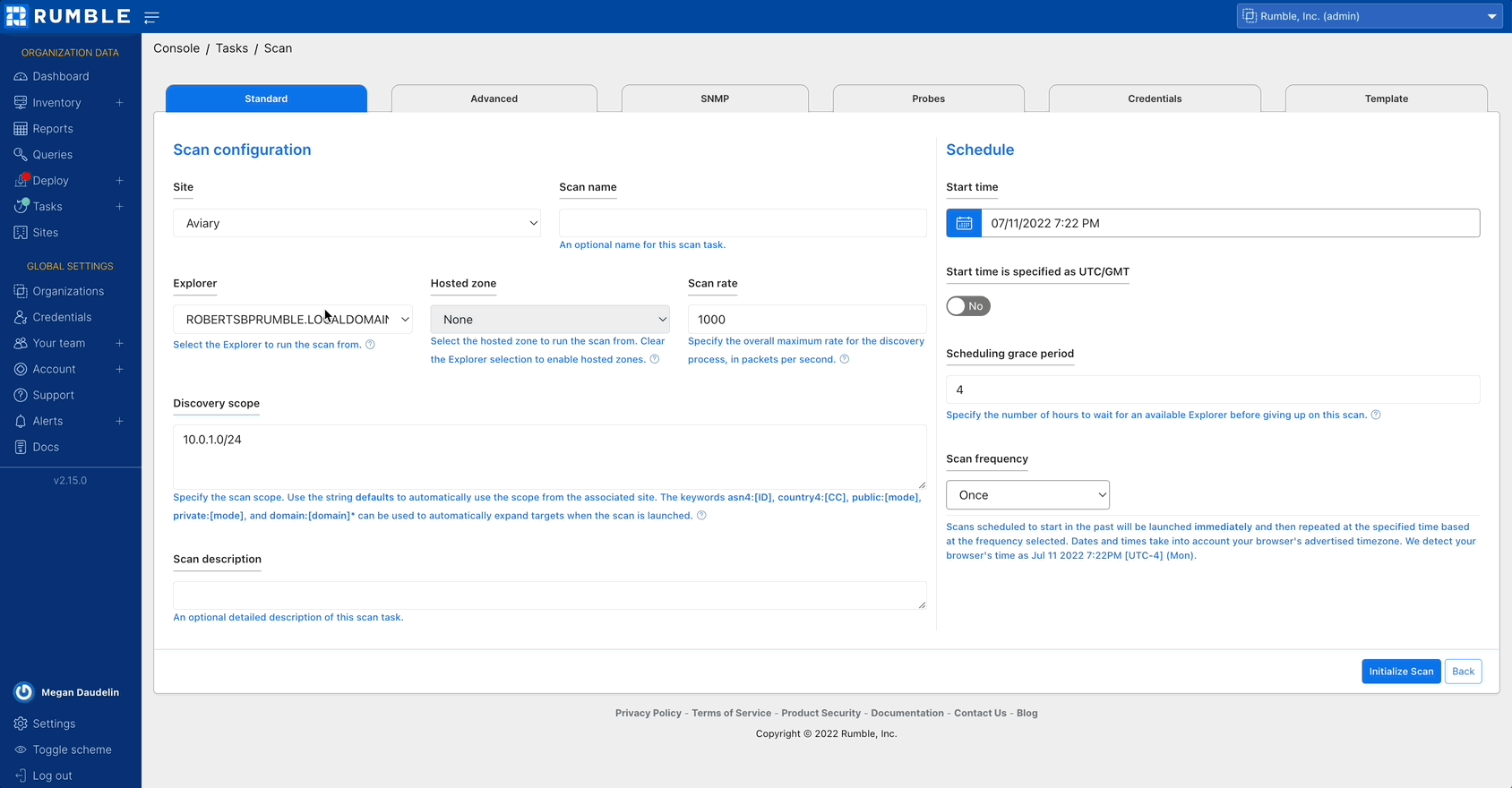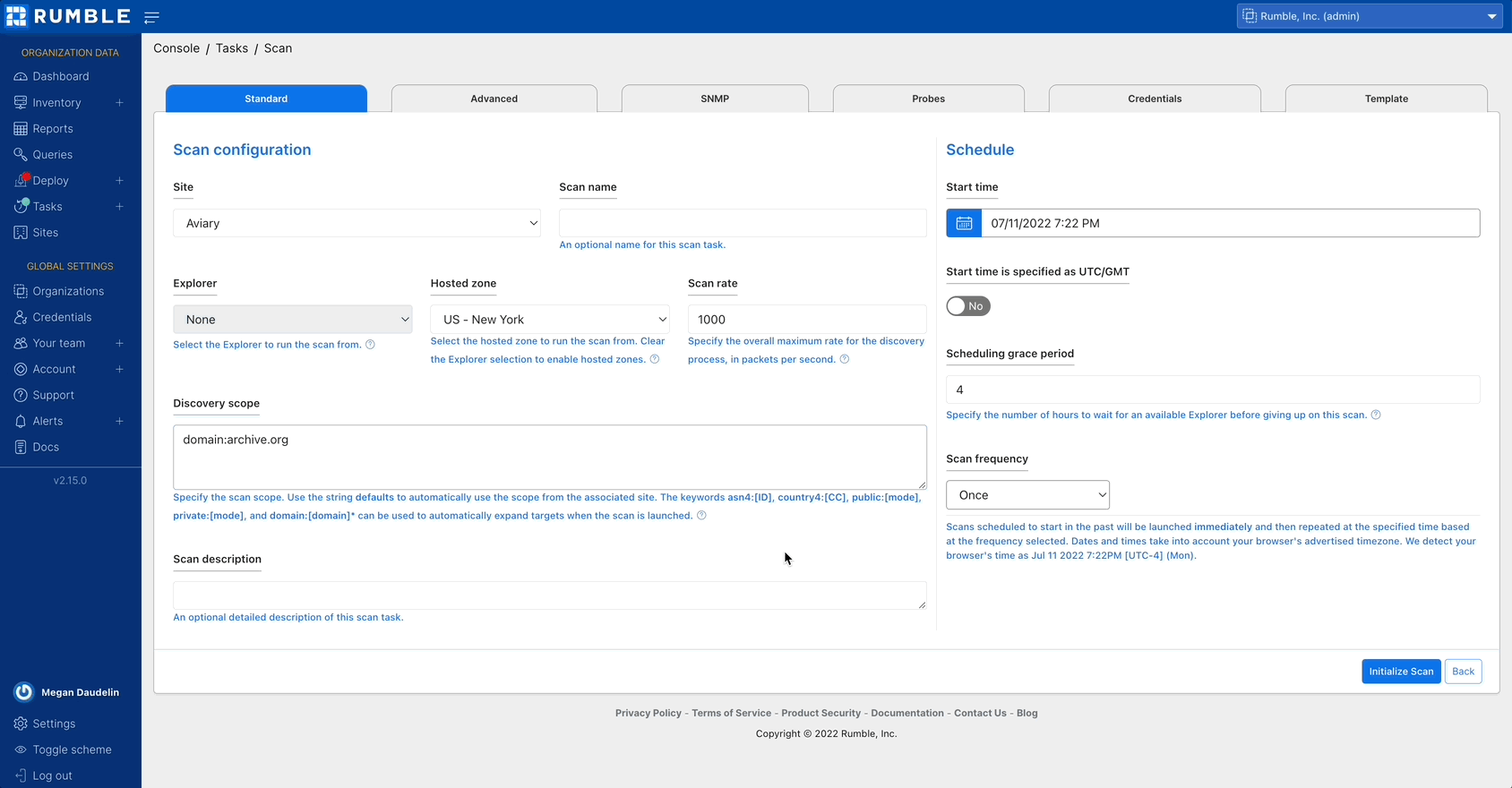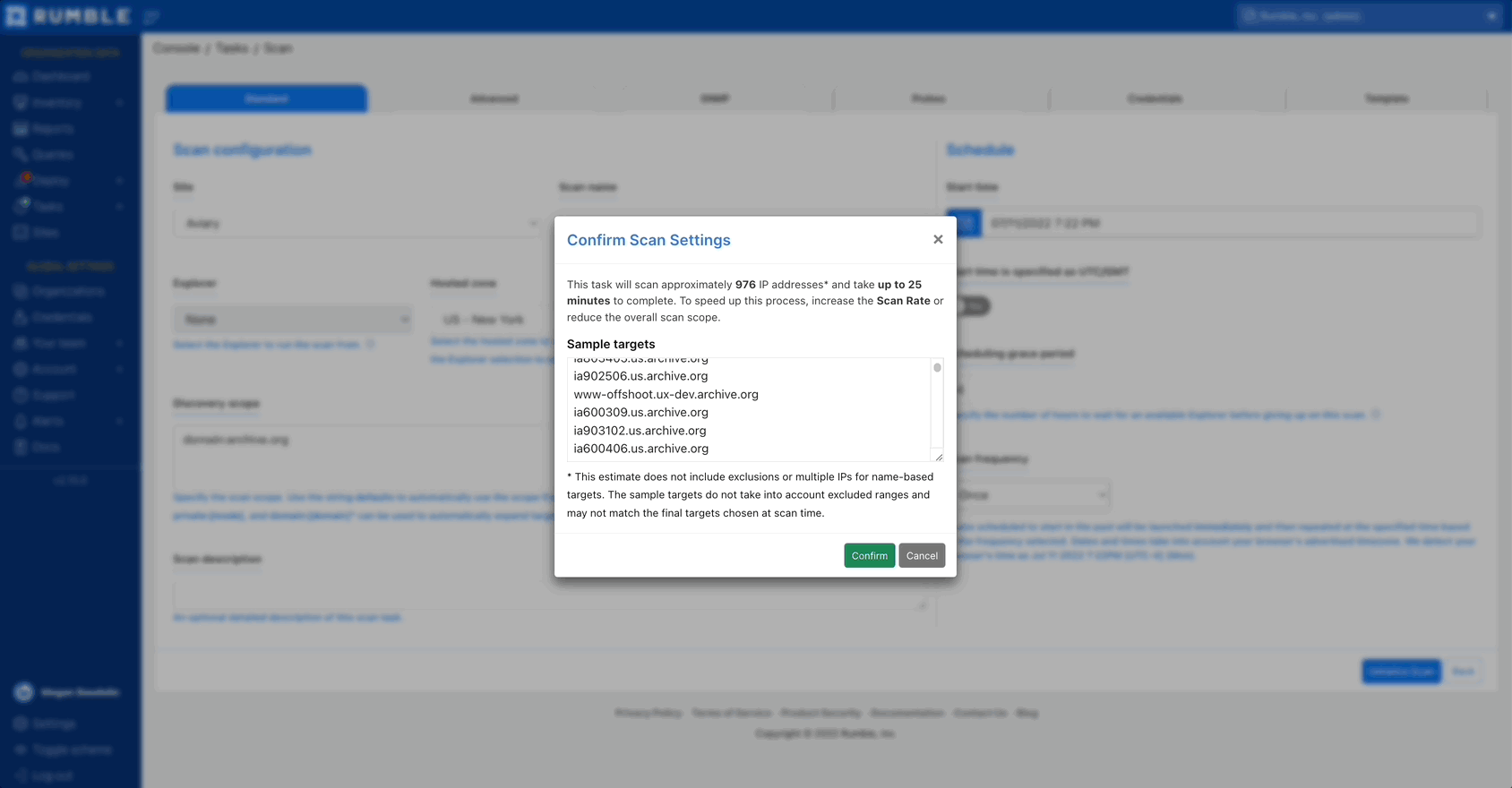
Finding externally exposed assets #
Rumble Enterprise customers using the cloud-hosted platform can now scan external assets easier than ever. To use a hosted scanner, set your Explorer to None and select a hosted zone during the scan configuration. Combine this with existing features to quickly discover external-facing assets and identify exposed services on cloud assets and endpoints that report external IP addresses through API connections.
Compatible keywords
The new domain:<example.com> keyword will automatically select publicly-known hostnames associated with a given domain. The new public:<mode> keyword now selects all external IPs within your organization based on the chosen mode (all, primary, or secondary). These keywords also work with the existing asn4:<ID> and country4:<CC> options. Keywords can be used as default site scopes, in recurring scans, and as exclusions. Combine keywords with existing integrations to automatically identify and scan external addresses associated with your assets.
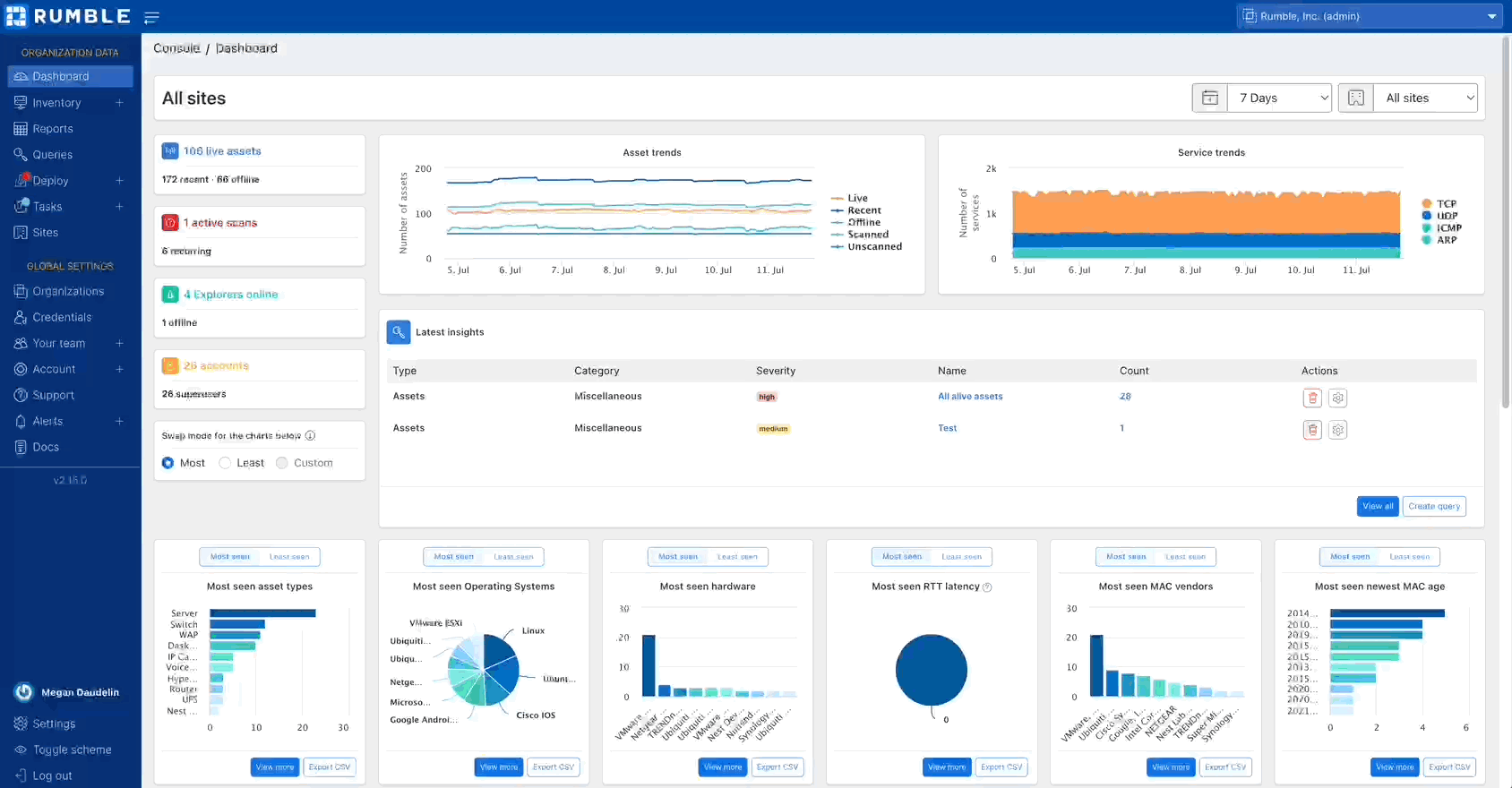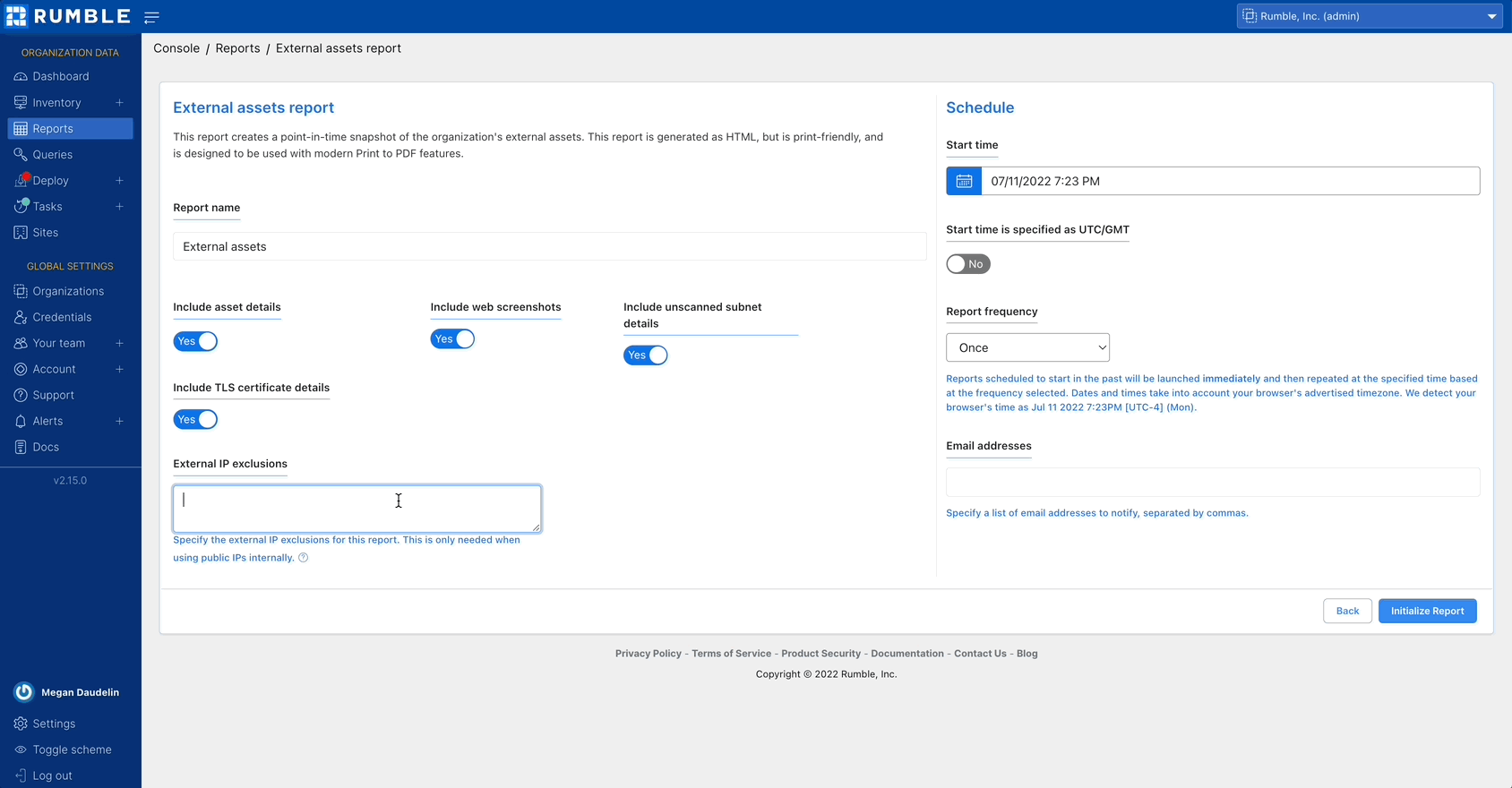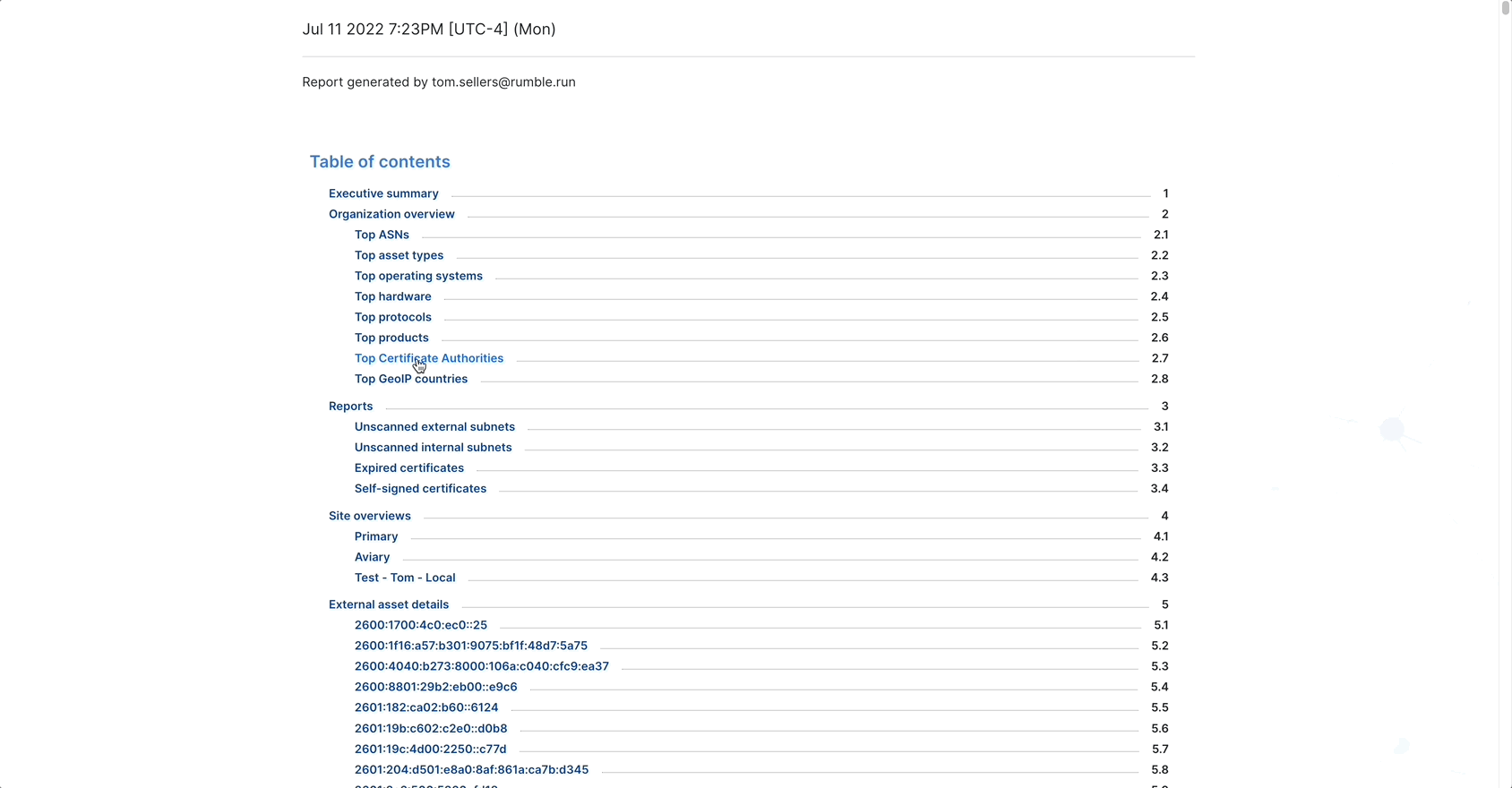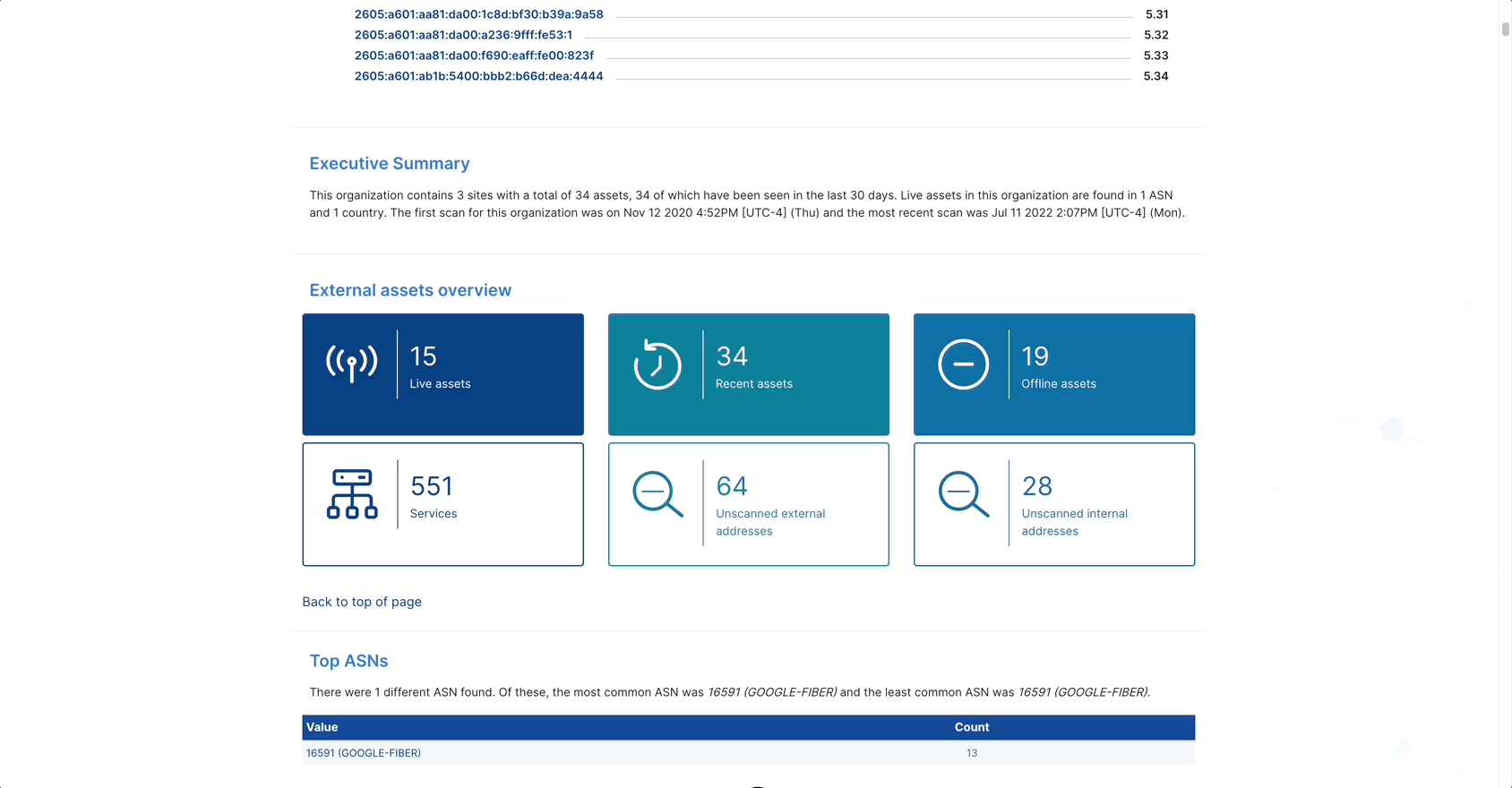
External Asset Report
For Rumble Enterprise users, the new External Asset Report provides a detailed overview of your external-facing assets and can optionally include asset details and web screenshots. This report can help you track down issues that may need resolution, such as assets that shouldn’t have public-facing interfaces and expired certificates. Once you’ve generated the report, you can click on results to quickly navigate to additional details in the Rumble Console. The report can be saved as HTML, printed as a PDF, shared via email, and scheduled to run recurrently.
Generate an External Asset Report from the Reports page.
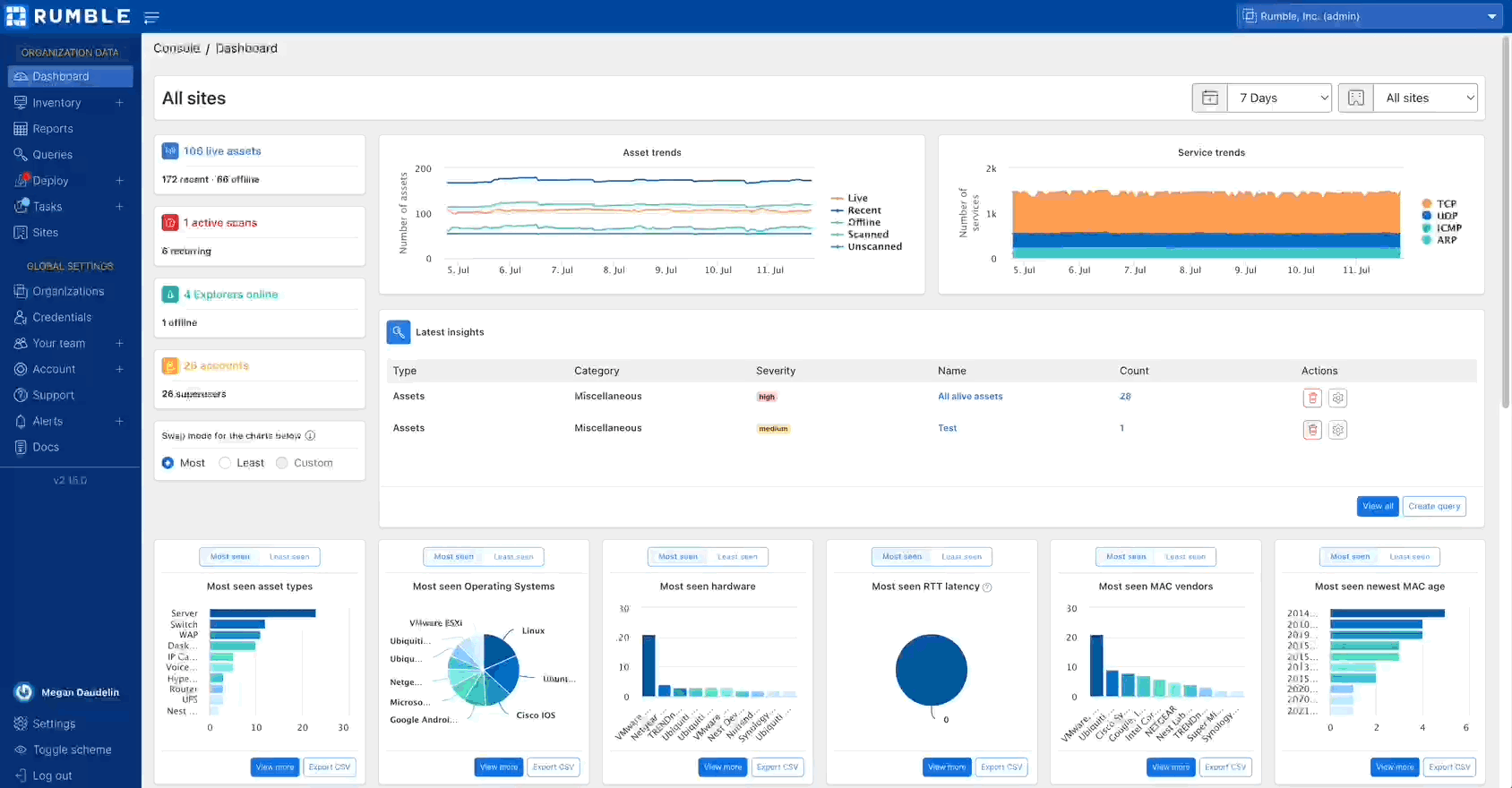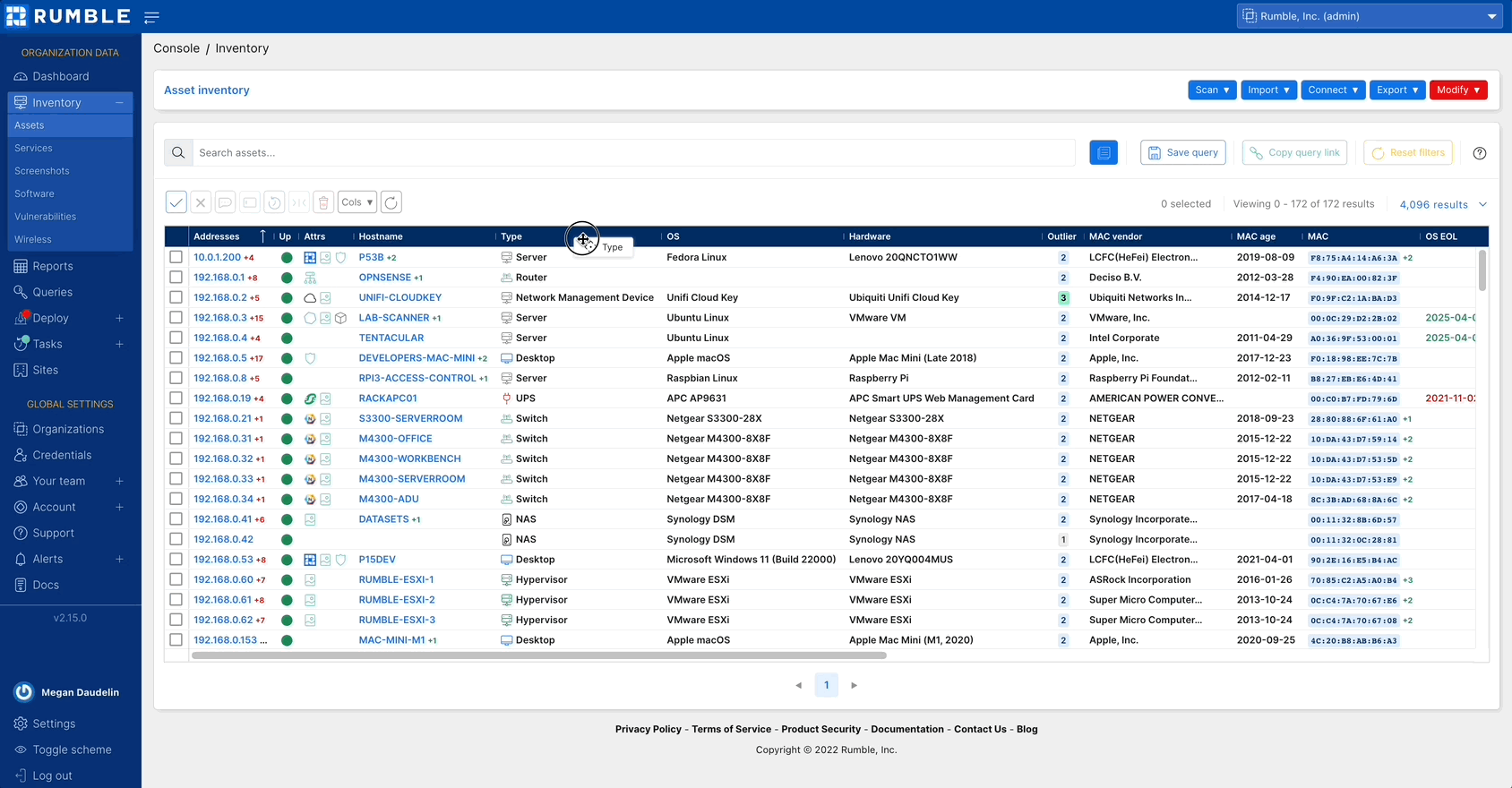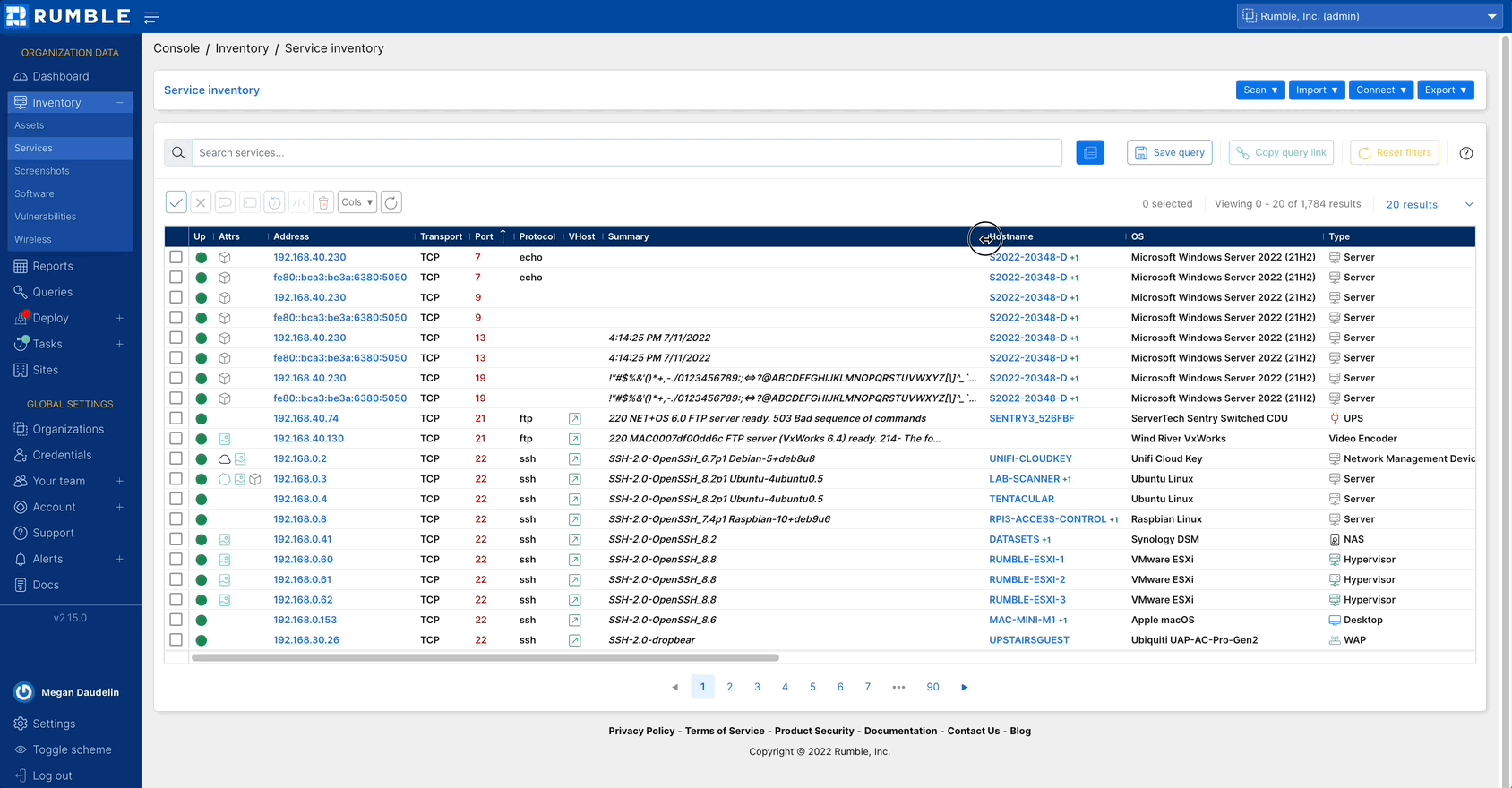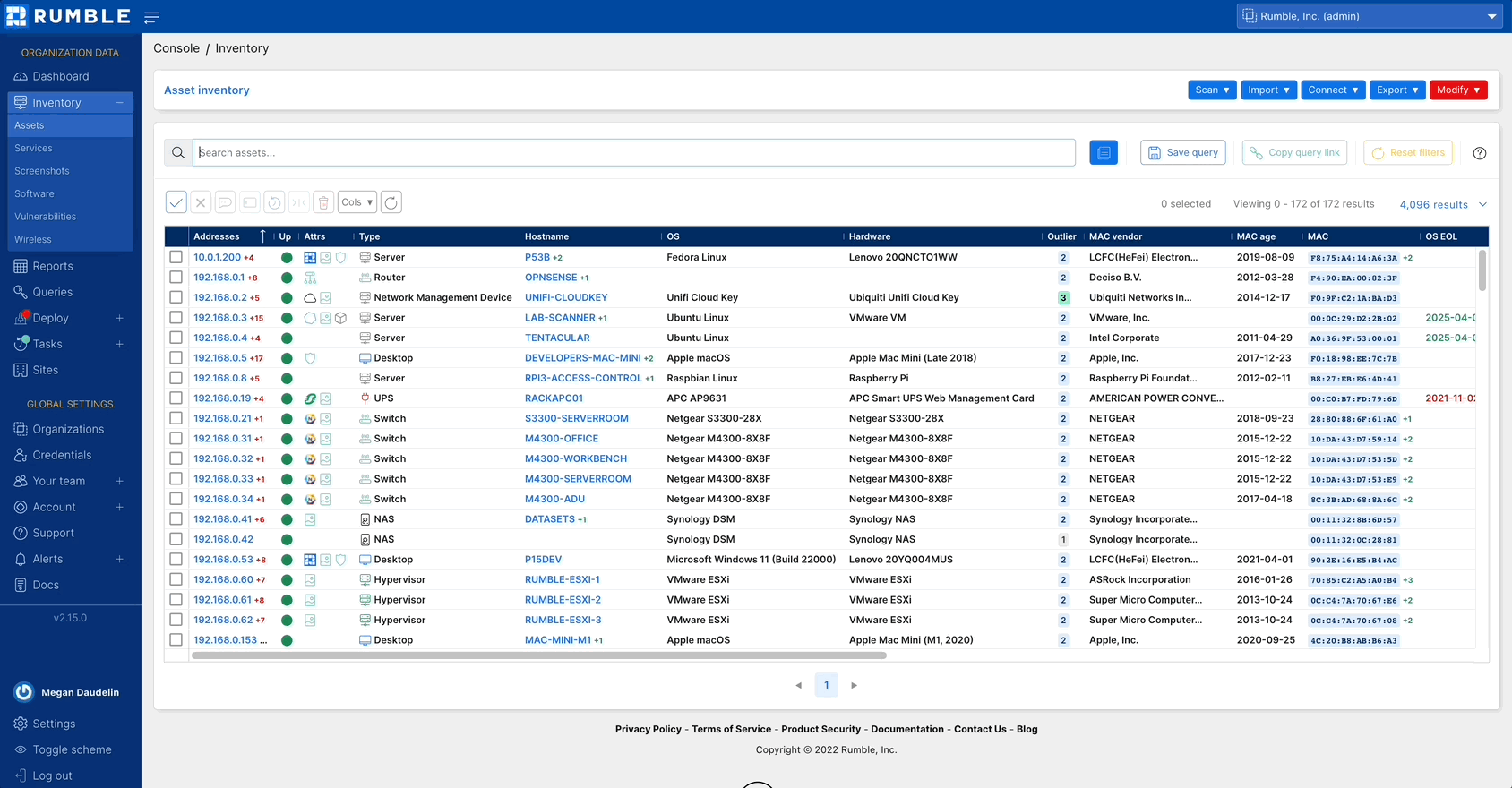
Navigating your Rumble inventory #
The inventory in your Rumble Console has been updated with several features to improve performance and usability. The number of results listed in the tables can be increased up to 4,096 and your columns can be resized, making viewing and querying results easier than ever.
Check out the changes to your asset inventory.
Release notes #
The Rumble 2.15 release includes a rollup of all the 2.14.x updates, which includes all of the following features, improvements, and updates.
New features #
- Rumble Enterprise customers can now sync asset and vulnerability data from the InsightVM API and upload data from Nexpose XML Export files.
- Rumble Enterprise customers can now sync asset, software, and vulnerability data from the Nessus Professional API.
- Scan scopes can now be populated using external domains and IP addresses.
- All inventory tables have been redesigned and are now more performant when displaying a large number of assets.
- Integration tasks have been renamed from "Import" to "Connector" and can now run in parallel while connecting to third-party APIs.
- Added new reports for Software, Vulnerabilities, and External Assets.
- The self-hosted platform install now supports Rocky Linux.
- Rumble Enterprise customers can now search inventory by hosted zone.
Product improvements #
- The scan engine now sets additional attributes for TLS certificates.
- Links to query language documentation have been updated throughout the product.
- The Account API now supports scan template management.
- The scan engine discovers additional services, including Elasticsearch, Logstash, and Prometheus.
- Query "address" keywords now support CIDR notation.
- The scan engine now sets additional attributes for TLS certificates.
- SSO configuration now skips IdP-provided encryption certificates during setup.
- Explorers deployed on macOS can now be transferred between organizations successfully.
- Last activity dates of users are now shown in the same time zone as the account creation date.
- A preview of software and vulnerability attributes is now displayed when hovering over the Click To Copy button on the Asset details page.
- The scan engine now flags TLS services with self-signed certificates and untrusted CAs.
- CSV exports of asset information now include OS EOL and extended OS EOL dates.
- Credentials limited to specific organizations can no longer be created by an administrator without access to the organizations.
- Additional validation for scan targets has been added to hosted scans.
- Asset inventory column selection and ordering now persist between queries.
- Connector tasks now obey the start time set when they are created.
Performance improvements #
- The Site edit page is now much faster for sites with large numbers of subnets.
- If the start time of a recurring task is changed, the change now saves successfully and queues an immediate run if appropriate.
- Explorer initialization speed has been optimized.
- The performance of the vulnerabilities table has been improved.
Fingerprinting changes #
- Improved fingerprint coverage for operating systems, including Linux, Windows, and more.
- Improved TLS certificate details via new attributes, including self-signed certificates and unknown certificate authorities.
- Added new capabilities for asset and service fingerprinting.
- Improved operating system fingerprinting of imported Tenable assets.
- A fingerprint for the Cockpit application has been added and includes additional Linux OS fingerprinting capability.
- General improvements in fingerprinting, including networking devices, KVMs, SIP devices, printers, and IP Cameras.
- Additional support for products by 2N, Algo, Allied Telesis, Amcrest, Arlo, Aruba Networks, Avaya, Avocent, Axis, Bosch, Cisco, Dahua, Dell, Eaton, Geist, GeoVision, Grandstream, Hanwha, Hikvision, Honeywell, Huawei, IBM, MikroTik, Nokia, Ricoh, SAS, Shelly, Telindus, TP-LINK, Ubiquiti, Verint, WAGO, and Zyxel.
Integration improvements #
- An API endpoint was added for Nessus imports.
- Date range queries now work on Tenable / Nessus attributes. (This requires a re-import of the appropriate data.)
- Censys Search data processed using file import is now handled correctly.
- Improved merging of AWS, Azure, and GCP assets imported from Tenable.io.
- The Tenable integration now includes an option to import unscanned assets and is disabled by default.
- The logic for merging Tenable/Nessus assets into the Rumble inventory has been improved.
- The accuracy of
first_seenandlast_seendates has been improved for Nessus imports. - The Tenable integration now provides more informative error messages for task failures due to invalid API keys and missing permissions.
- Additional validation for Tenable.io credentials has been added.
Bug fixes #
- A bug that affected JSON exports of task information has been resolved.
- A bug that delayed task processing when many vulnerability records were present has been resolved.
- A bug has been fixed that prevented assets missing certain date/time fields from being imported from a Nessus file.
- A bug has been fixed that prevented using boolean search terms with the Vulnerabilities table.
- A bug has been fixed that prevented some customers from importing assets from SentinelOne.
- A bug was fixed with SentinelOne credential creation.
- A bug was fixed which could result in an incorrect agent ID or template ID being written to tasks when they were updated via API.
- A bug was fixed which prevented the asset route pathing report from rendering the source name properly in the report heading.
- A bug that prevented customer address information from being validated has been resolved.
- A bug that prevented SSO settings from being updated correctly has been resolved.
- A bug in the scan engine that could lead to unexpected printer output has been resolved.
- A bug in the e-commerce checkout with non-US addresses has been resolved.
- A bug that could cause the Explorer service to timeout on startup has been resolved.
- A bug has been fixed that could occasionally cause site deletion to trigger creation of an unnecessary site.
- A bug that caused software and vulnerabilities to be ignored when manually merging assets has been fixed.
- A bug that could prevent task configuration from showing the list of available explorers has been fixed.
- A bug that could prevent using the console to contact support has been fixed.
- A bug that prevented filtering some Fortinet Web Filter replies has been fixed.
- A bug that could cause hosted scans to timeout after an hour has been resolved.
- A bug that prevented viewing third-party attributes for assets without Rumble attributes has been resolved.
- A bug that affected the first seen and last seen dates for assets imported from Tenable.io and Nessus has been resolved.
- A bug that persisted a task’s error message when copying the task has been resolved.
- A bug that could prevent the Tenable connector from importing large sites has been resolved.