Wrapping up 2021 and kicking off 2022, there were no shortages of vulnerabilities, vendor security advisories, patches, and active exploitations. Oh, did we mention, even more vulnerabilities and more patches? To ring in 2022 accordingly, let's discuss some recent notable vulnerabilities (including an update on heavy-hitter Log4j) and touch on some CISA updates to their Known Exploited Vulnerabilities Catalog.
Wormable Windows vuln in the HTTP protocol stack (CVE-2022-21907) #
As part of Patch Tuesday his week, Microsoft patched a vulnerability that could leave modern Windows systems (including Windows 10, Windows 11, and also Windows Server 2019 and 2022) open to exploitation. Existing within the HTTP Trailer Support logic of the HTTP protocol stack, this vulnerability is tracked as CVE-2022-21907 and has a "critical" CVSS score of 9.8. Considered "low complexity" to exploit, successful exploitation does not require authentication and can yield remote code execution to an attacker. Microsoft encourages patching of vulnerable systems, and does also offer mitigation steps for Windows 10 and Windows Server 2019 systems.
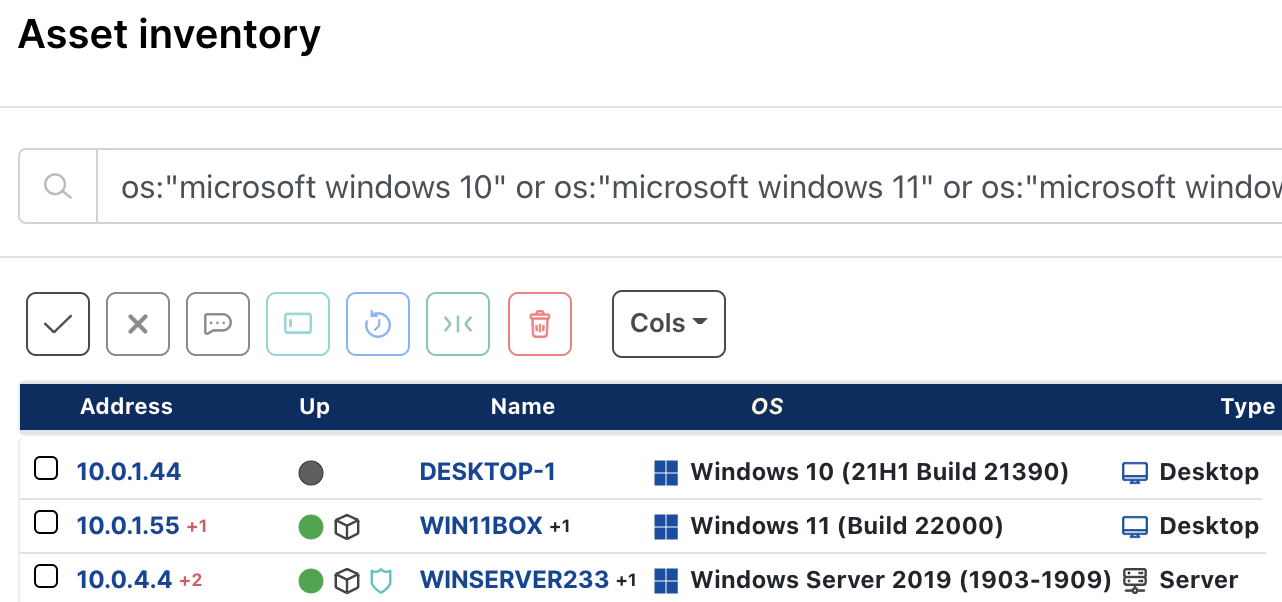
You can search for potentially vulnerable Windows instances in your network inventory with the following runZero asset inventory query:
os:"microsoft windows 10" or os:"microsoft windows 11" or os:"microsoft windows server 2019" or os:"microsoft windows server 2022" or (os:="microsoft windows" and os_version:="")
Multi-vendor router flaw in the NetUSB kernel module (CVE-2021-45608) #
Recently published security research from SentinelOne surfaced a vulnerability in the NetUSB kernel module from KCodes, which is used by a number of manufacturers in many popular home and small-business routers, including (but not limited to) the following:
- D-Link
- EDiMAX
- Netgear
- Tenda
- TP-Link
- Western Digital
Designed to support USB over IP, the NetUSB module contains an integer overflow vulnerability which can be successfully exploited (pre-authentication) to trigger a denial-of-service on the target router or even remote code execution (for more-advanced attackers). Tracked as CVE-2021-45608, this vulnerability received a "critical" CVSS score of 9.8 and folks with vulnerable router devices should upgrade to patched firmware releases as available.
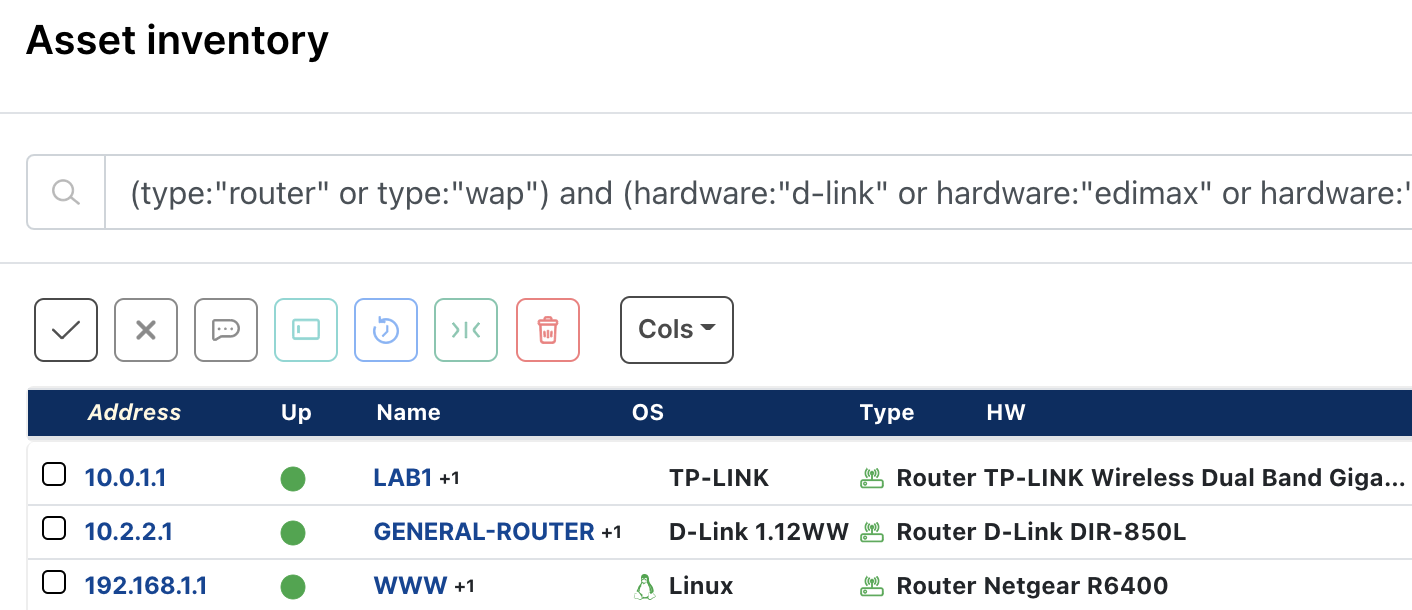
You can search for potentially vulnerable routers in your network inventory with the following runZero asset inventory query:
(type:"router" or type:"wap") and (hardware:"d-link" or hardware:"edimax" or hardware:"netgear" or hardware:"tenda" or hardware:"tp-link" or hardware:"western digital")
And speaking of large-impact vulnerabilities…
Circling back on Log4j #
Log4j vulnerabilities became a whirlwind of activity last month, involving an 0-day and disclosures, newly patched releases, active exploitation, vendor security advisories, downstream software pulling-and-including new Log4j releases, and many (so many) end users patching and mitigating as best they could.
With an astoundingly far-and-wide reach in affected applications/software, four CVEs ultimately shook out of all of this:
- CVE-2021-44228 - could allow remote code execution via lookup-with-JNDI vulnerability ("critical" CVSS score of 10.0)
- CVE-2021-45046 - could allow remote and/or local code execution via lookup-with-JNDI vulnerability ("critical" CVSS score of 9.0)
- CVE-2021-45105 - could allow DDoS via infinite recursion vulnerability ("high" CVSS score of 7.5)
- CVE-2021-44832 - could allow remote code execution via JDBC Appender with a JNDI LDAP data source URI vulnerability ("medium" CVSS score of 6.6)
Per Apache's guidance, folks should be using the latest versions of Log4j to remediate thes vulns, which include:
- v2.17.1 (for Java 8 and later)
- v2.12.4 (for Java 7)
- v2.3.2 (for Java 6)
While many affected vendors did publish details on their affected products (and offer patched solutions and/or mitigations for their users/customers), a small number of vendors have chosen to make these details only available to their customers with current support contracts, and some vendors are still referring to their investigations into affected products as "ongoing".
Government entities who stepped up to help sort through affected vendors and products may be the best bet as a long-term source for ongoing Log4j updates, including (but not limited to):
You can read more details, plus access many easy-to-use runZero searches to help surface potentially vulnerable products in your network, in our Log4j blog post.
New CISA guidance to patch against 15 exploited vulns #
Rounding out our post today, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) recently added 15 vulnerabilities to the Known Exploited Vulnerabilities Catalog it maintains "based on evidence that threat actors are actively exploiting" these vulnerabilities. While some vulnerabilities are ones from fairly recent memory, others go back a number of years. While CISA's posted remediation due dates (which U.S. FCEB agencies are required to honor via BOD 22-01) include later this month (for a handful of the vulns) and July 2022 (for the remaining vulns), CISA "strongly urges all organizations to reduce their exposure to cyberattacks by prioritizing timely remediation of Catalog vulnerabilities as part of their vulnerability management practice."
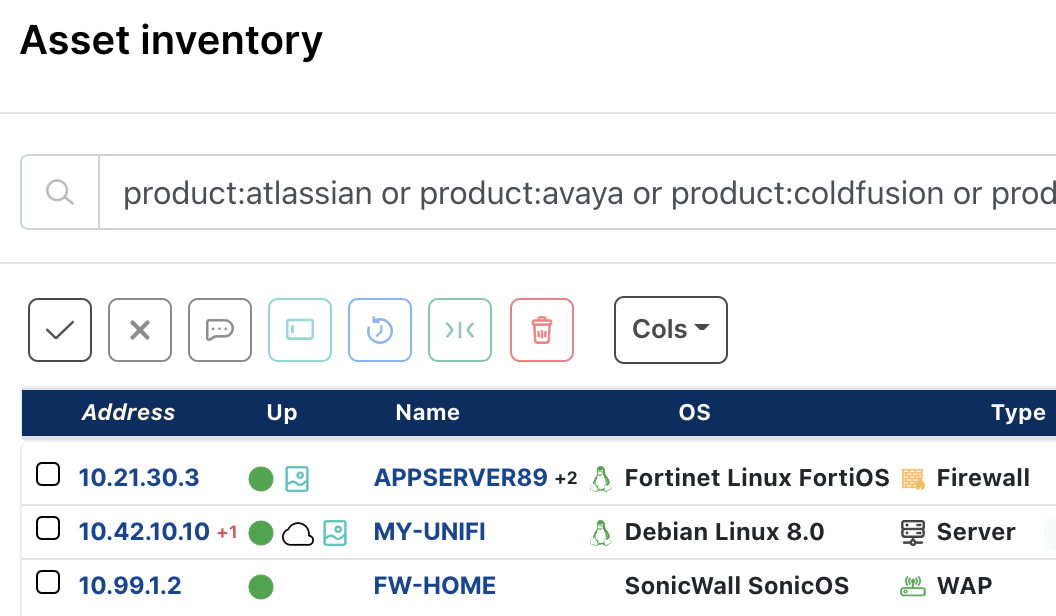
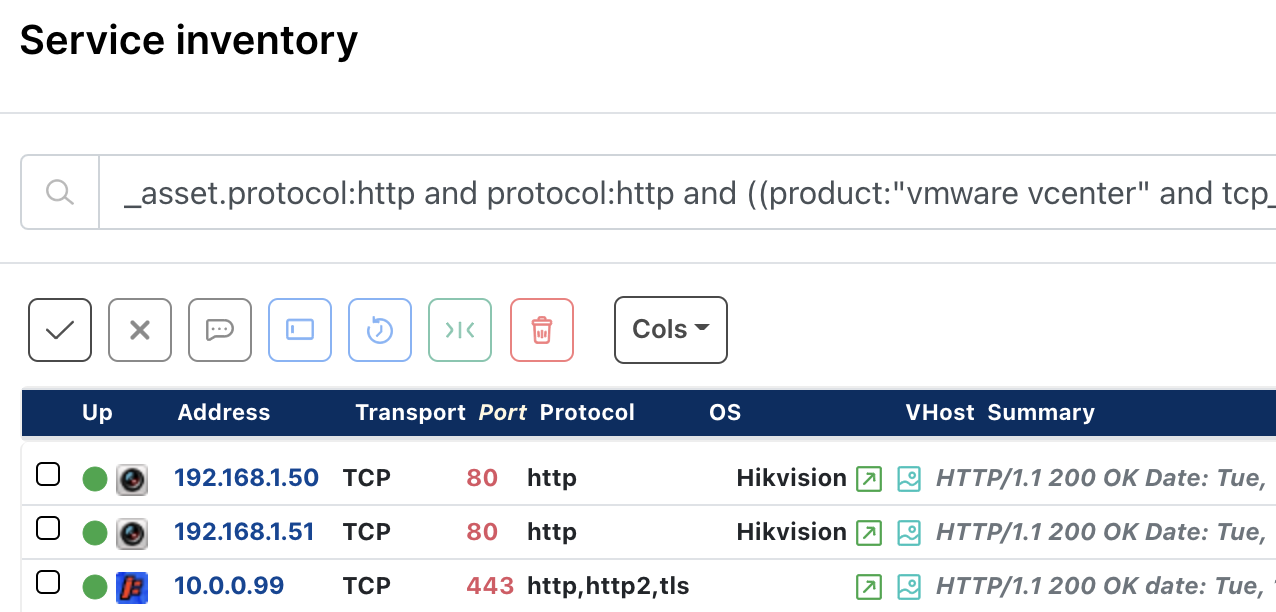
You can search your network inventory for the handful of vulnerabilities that have a CISA January 2022 remediation due date using the following runZero service inventory query:
_asset.protocol:http and protocol:http and ((product:"vmware vcenter" and tcp_port:443) or (_asset.vendor:hikvision or hw:hikvision) or (_asset.protocol:http and protocol:http and (html.title:"FatPipe IPVPN" or last.html.title:"FatPipe IPVPN" or html.title:"FatPipe MPVPN" or last.html.title:"FatPipe MPVPN" or html.title:"FatPipe WARP" or last.html.title:"FatPipe WARP")))
Try runZero #
Don't have runZero and need help finding assets potentially vulnerable to items in this blog post? Start your runZero trial today.