Rumble Network Discovery collects a ton of information by default. SSH versions, pre-authentication banners, and SSH host keys are collected regardless of what port SSH is running on. SSH host keys in particular are an example of something that should always be unique on the network, but often isn't, with real-world security implications.
Unless you knew what the value of the duplicate SSH key was, this used to be a difficult problem to solve. Vulnerability scanners could find known bad SSH keys but they don't look for duplicate keys. The best way to find duplicates is to scan everything and then pivot over the SSH host key field to find keys shared between assets.
Rumble can do this very easily. In fact, you can pivot on any device property, which makes finding outliers a breeze. It helps you find orphaned devices, drifts in patch levels, and much more.
How Duplicate SSH Host Keys Put Your Network At Risk #
For SSH, each host should have a unique host key. An SSH host key is typically generated when OpenSSH is first installed or when the computer is first booted. When you clone a host, for example from a virtual machine image, the SSH host key is likely also cloned. Now both computers will use the same encryption key for SSH sessions. This becomes a problem in various scenarios.
First, if you are cloning the machine from a publicly available image, an attacker could decrypt the SSH traffic through a man-in-the-middle (MITM) attack because they have access to the public and private portions of your SSH host key. The same is true for using IoT devices that use the same SSH host key in the firmware. When an attacker buys one device, or obtains a downloadable copy of the firmware, they can decrypt traffic, including clear-text credentials and session data on all other devices using the same key.
Second, even if your SSH host key is from an internal, trusted image, you're putting the organization at risk. If any of the machines with the same SSH host key is compromised, for example through a vulnerability or default credentials, the attacker now has a copy of your SSH host key which is shared by all other machines and can use this to move laterally through your network.
How to Find Duplicate SSH Host Keys on Your Network #
Rumble is a network discovery product that uses unauthenticated scans to inventory your network (free trial here). Rumble collects the hash of each host in the property ssh.hostKey.md5.
Let's have a look how to do this using a test data set of the publicly available IP space of Iceland.
Start out by finding all live assets on your network that are running SSH. In the left navigation, go to Inventory and type the following into your search bar:
alive:t protocol:ssh
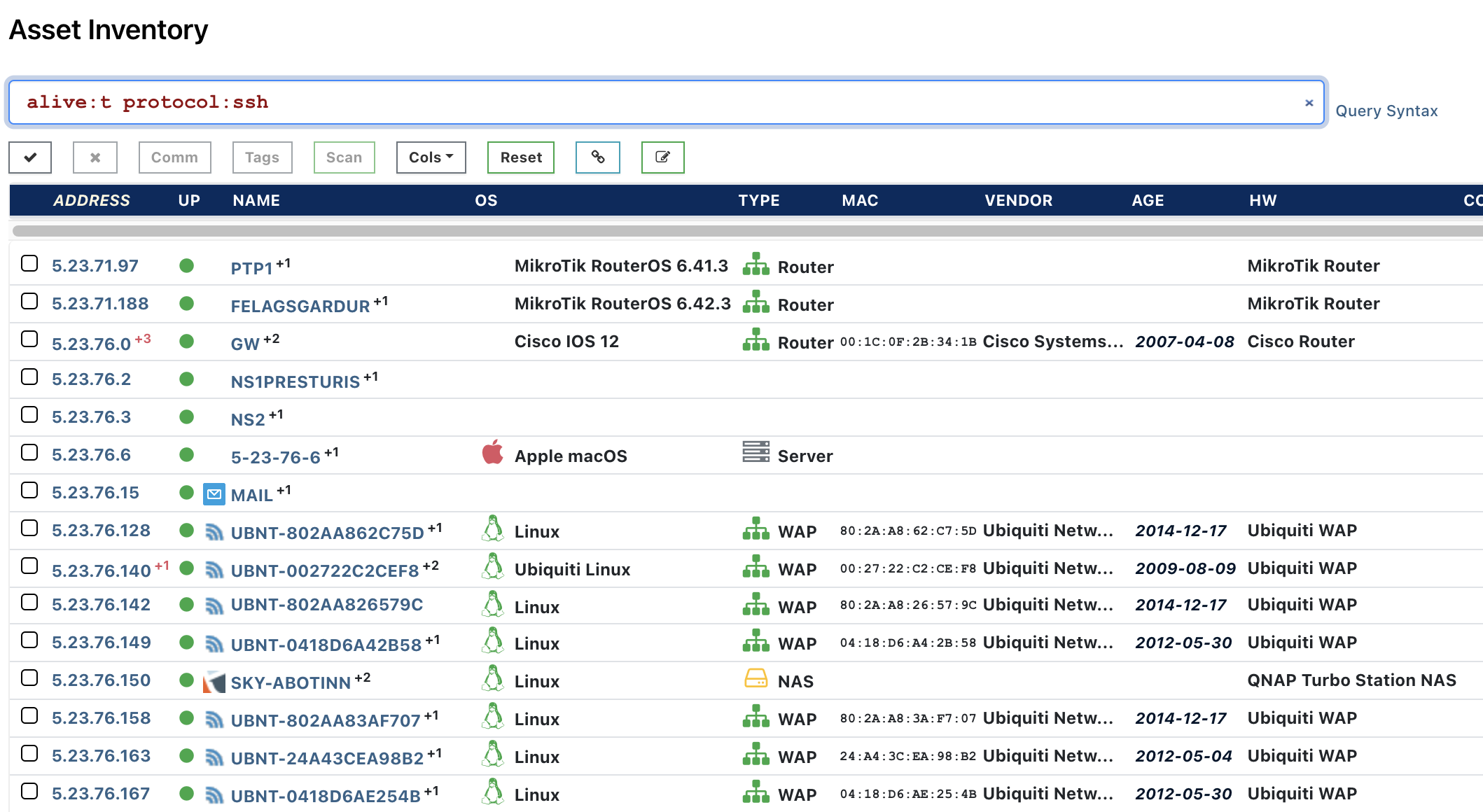
Next, click on any of the hosts to view the properties of any of the hosts. Search the page for "MD5" until you find the property ssh.hostKey.md5.
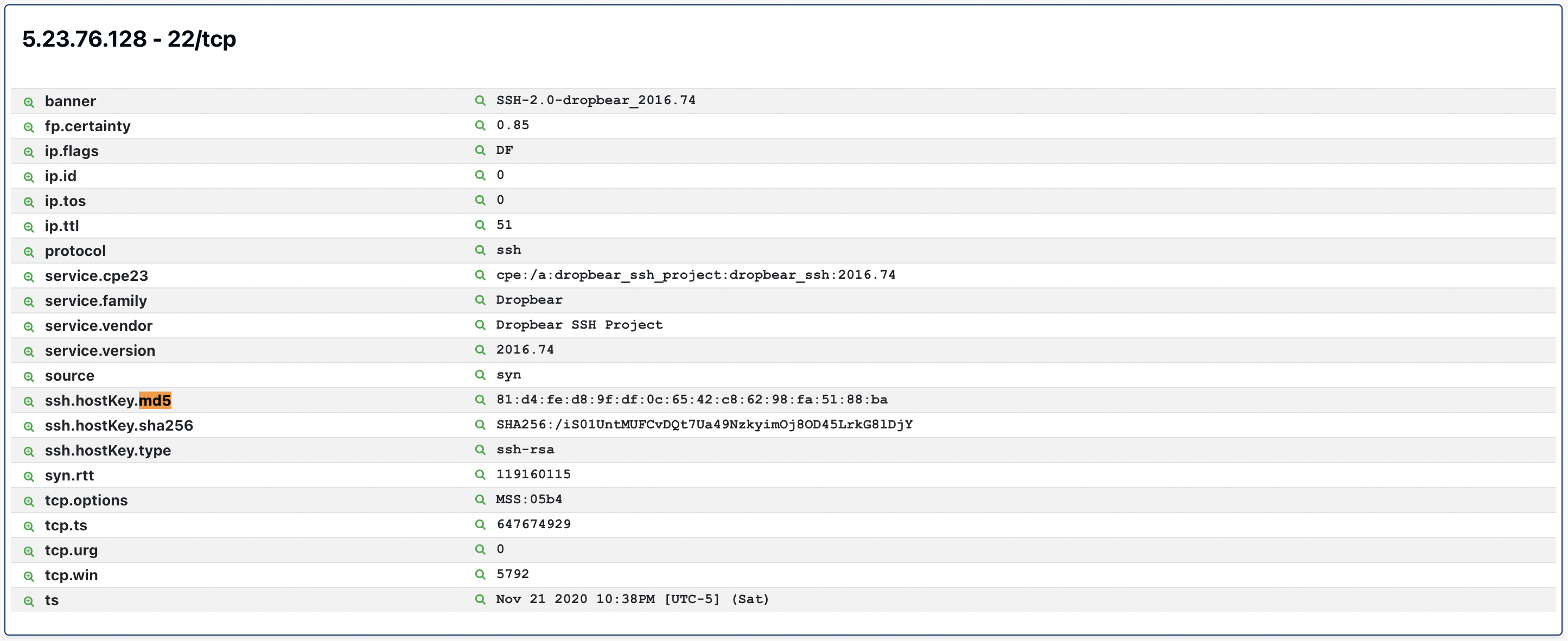
Click on the small magnifying glass icon to the left of ssh.hostKey.md5 to pivot over the SSH Host Key to view a count of all of the SSH host key hashes in decreasing order.
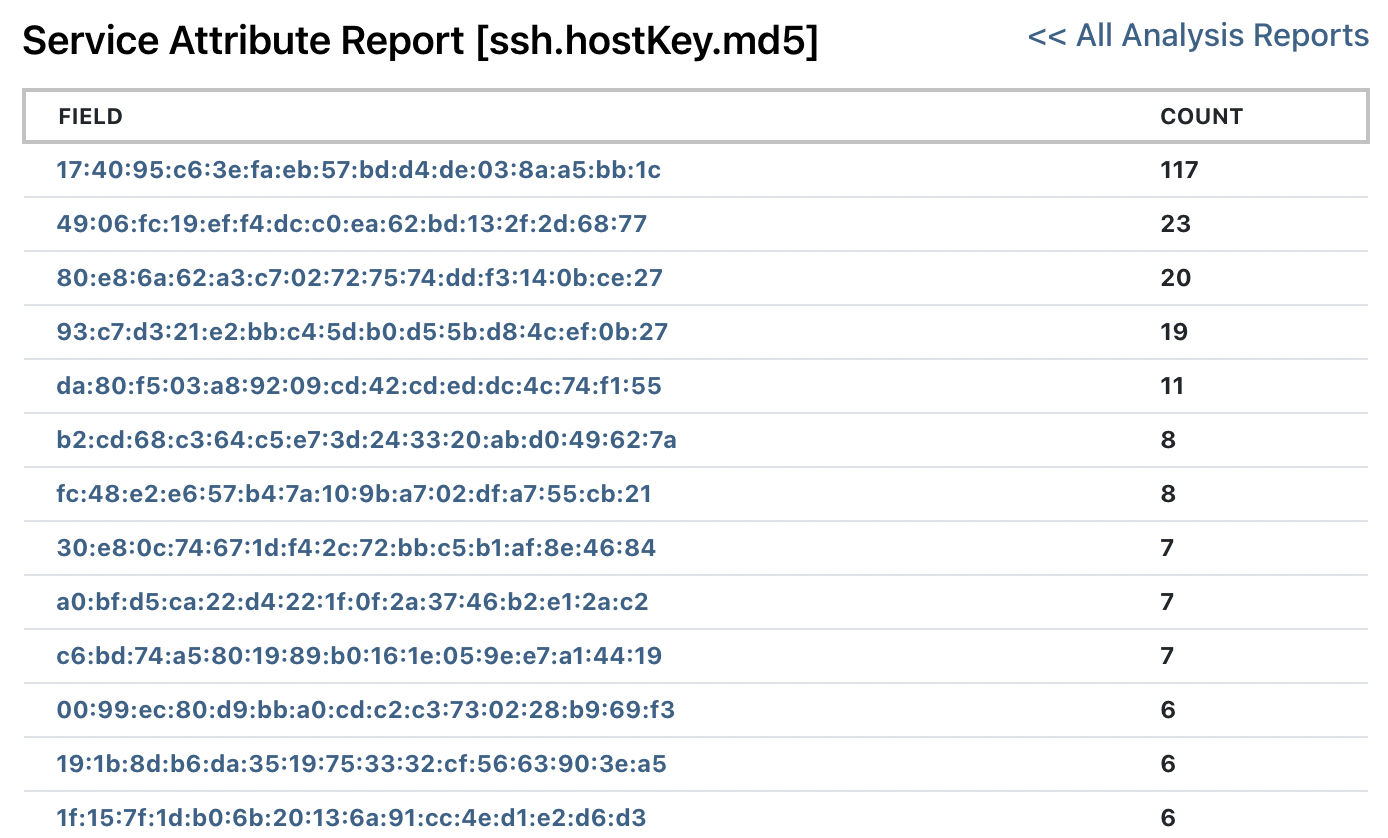
If you see any count larger than 1, you have a duplicate SSH key on the network. The 117 devices in the Iceland sample set are from the same IoT device manufacturer.
Try Finding Duplicate SSH Keys on Your Network with Rumble #
If you haven't had a chance to try runZero, or would like to play with the new features, sign up for a free trial and let us know what you think!